SharkBot abuses accessibility permissions in a number of methods to conduct its malicious endeavor. The malware can steal consumer credentials by logging textual content entered into login fields. Within the case {that a} consumer’s account is protected by SMS two-factor authentication (2FA), SharkBot can bypass this safety by studying SMS messages to steal authentication codes. The malware can be able to overlaying faux login screens instantly over focused monetary apps. The faux login screens seem legit however truly steal entered consumer credentials. Moreover, risk actors can use SharkBot to remotely management contaminated gadgets. All of those capabilities are scary sufficient, however a brand new model of SharkBot has entered the wild with the additional capability to steal consumer session cookies.
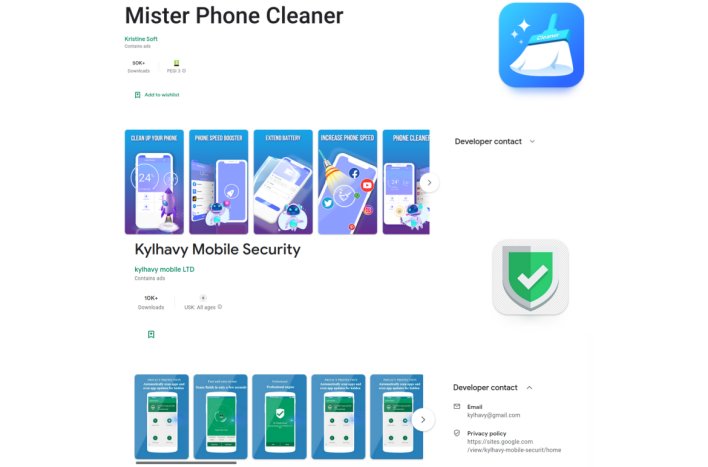
The researchers discovered two apps on the Google Play Retailer that include this up to date malware dropper: Mister Cellphone Cleaner and Kylhavy Cell Safety. Between them, the 2 apps have a complete of 60,000 downloads. As of the time of writing, Google seems to have eliminated the Kylhavy Cell Safety app from the Play Retailer however hasn’t but delisted Mister Cellphone Cleaner. Hopefully, Google will take away the latter app shortly, however eradicating an app from the Play Retailer gained’t take away it from affected customers’ gadgets. These with these malicious apps already put in on their gadgets might want to manually take away the apps themselves.


