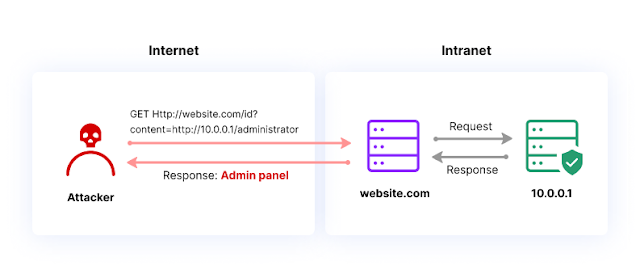
autoSSRF is your greatest ally for figuring out SSRF vulnerabilities at scale. Totally different from different ssrf automation instruments, this one comes with the 2 following authentic options :
-
Sensible fuzzing on related SSRF GET parameters
When fuzzing, autoSSRF solely focuses on the widespread parameters associated to SSRF (
?url=,?uri=, ..) and doesn’t intervene with every little thing else. This ensures that the unique URL remains to be accurately understood by the examined web-application, one thing which may doesn’t occur with a instrument which is blindly spraying question parameters. -
Context-based dynamic payloads technology
For the given URL :
https://host.com/?fileURL=https://authorizedhost.com, autoSSRF would acknowledge authorizedhost.com as a doubtlessly white-listed host for the web-application, and generate payloads dynamically based mostly on that, trying to bypass the white-listing validation. It will consequence to fascinating payloads akin to :http://authorizedhost.attacker.com,http://authorizedhost%[email protected], and many others.
Moreover, this instrument ensures nearly no false-positives. The detection depends on the nice ProjectDiscovery’s interactsh, permitting autoSSRF to confidently determine out-of-band DNS/HTTP interactions.
Utilization
This shows assist for the instrument.
utilization: autossrf.py [-h] [--file FILE] [--url URL] [--output] [--verbose]choices:
-h, --help present this assist message and exit
--file FILE, -f FILE file of all URLs to be examined towards SSRF
--url URL, -u URL url to be examined towards SSRF
--output, -o output file path
--verbose, -v activate verbose mode
Single URL goal:
python3 autossrf.py -u https://www.host.com/?param1=X¶m2=Y¶m2=ZA number of URLs goal with verbose:
python3 autossrf.py -f urls.txt -vSet up
1 – Clone
git clone https://github.com/Th0h0/autossrf.git2 – Set up necessities
Python libraries :
cd autossrf
pip set up -r necessities.txtInteractsh-Consumer :
License
autoSSRF is distributed below MIT License.