Researchers from Confiant have revealed their findings detailing an intensive malware marketing campaign the researchers are calling SeaFlower. The marketing campaign is focused at customers of 4 totally different cryptocurrency wallets on iOS and Android: MetaMask, Coinbase Pockets, imToken Pockets, and TockenPocket Pockets. The risk actors behind SeaFlower to talk Chinese language, judging by code feedback written in Chinese language, together with plenty of different indicators famous by the researchers. The risk actors additionally look like concentrating on different Chinese language audio system most closely, having carried out an search engine marketing poisoning marketing campaign that has most affected search outcomes from the Chinese language-based Baidu search engine. search engine marketing poisoning campaigns leverage search engine marketing (search engine marketing) methods to spice up malicious web sites into the highest search outcomes for reliable web sites or companies.
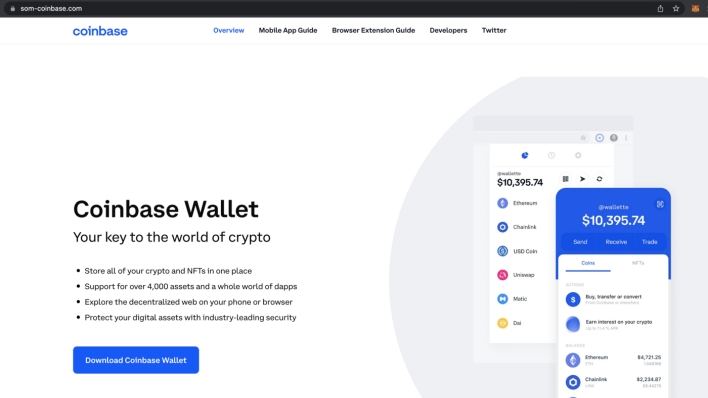
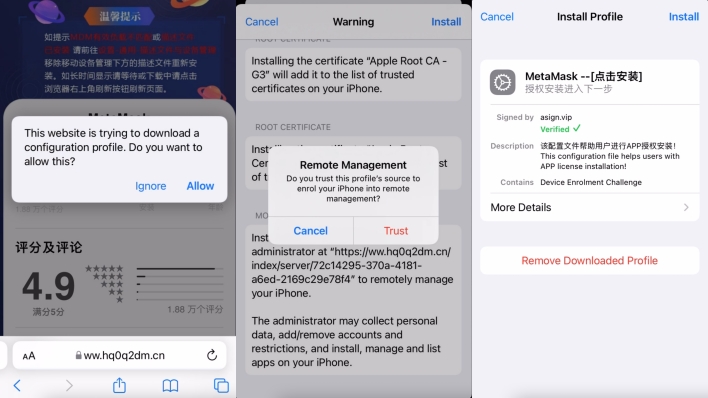
On this case, the risk actors have efficiently boosted malicious clones of internet sites for reliable cryptocurrency pockets. The malicious web sites seem equivalent to their reliable counterparts, however are hosted at domains managed by the risk actors. The malicious web sites embody obtain buttons for Android and iOS apps, however, relatively than redirecting customers to the Google Play Retailer or the Apple App Retailer, the buttons as a substitute try and side-load apps onto customers’ gadgets.
As soon as put in, the malicious apps seem and performance identically to the reliable cryptocurrency pockets apps they mimic. Nevertheless, the malicious apps include backdoors that log the pockets seed phrases, addresses, and balances and ship that info to the risk actors behind the marketing campaign. The risk actors can then use the seed phrases to hold out the account restoration course of and acquire entry to the funds in victims’ wallets. In some instances, the code containing the backdoors is encrypted, that means anybody inspecting the code for malicious conduct should first use the included cryptographic keys to decrypt the malicious code earlier than discovering what the code does.
To be able to keep away from falling prey to a malicious app marketing campaign resembling this one, iOS customers ought to by no means permit exterior provisioning profiles to be put in on their gadgets, and Android customers ought to set up apps solely from trusted sources. All the pockets apps focused by this specific assault could be discovered within the Google Play Retailer and Apple App Retailer, so customers ought to obtain and set up them there.
The researchers have offered the hashes for one of many malicious Android apps and all 4 malicious iOS apps distributed as a part of the SeaFlower marketing campaign, so others can determine the malicious apps.
Coinbase Pockets Android app
SHA-256 of the APK:
83dec763560049965b524932dabc6bd6
Coinbase Pockets iOS app
SHA-256 of the .IPA analyzed:
2334e9fc13b6fe12a6dd92f8bd65467cf
MetaMask iOS app
SHA-256 .IPA file analyzed:
9003d11f9ccfe17527ed6b35f5fe33d28
imToken Pockets iOS app
SHA-256 of the .IPA analyzed:
1e232c74082e4d72c86e44f1399643ff
TokenPocket iOS Pockets
SHA-256 of the .IPA file analyzed:
46002ac5a0caaa2617371bddbdbc7eca
74cd9cb48878da0d3218a78d5be7a53a


