bomber is an utility that scans SBOMs for safety vulnerabilities.
Overview
So you have requested a vendor for an Software program Invoice of Supplies (SBOM) for one in every of their closed supply merchandise, they usually offered one to you in a JSON file… now what?
The very first thing you are going to wish to do is see if any of the parts listed contained in the SBOM have safety vulnerabilities, and what sort of licenses these parts have. This may enable you determine what sort of threat you may be taking over by utilizing the product. Discovering safety vulnerabilities and license info for parts recognized in an SBOM is precisely what bomber is supposed to do. bomber can learn any JSON or XML primarily based CycloneDX format, or a JSON SPDX or Syft formatted SBOM, and inform you fairly shortly if there are any vulnerabilities.
What SBOM codecs are supported?
There are fairly a number of SBOM codecs accessible at this time. bomber helps the next:
Suppliers
bomber helps a number of sources for vulnerability info. We name these suppliers. At the moment, bomber makes use of OSV because the default supplier, however it’s also possible to use the Sonatype OSS Index.
Please word that every supplier helps completely different ecosystems, so should you’re not seeing any vulnerabilities in a single, attempt one other. It is usually necessary to know that every supplier might report completely different vulnerabilities. If doubtful, have a look at a number of of them.
If bomber doesn’t discover any vulnerabilities, it does not imply that there are not any. All it means is that the supplier getting used did not detect any, or it would not help the ecosystem. Some suppliers have vulnerabilities that come again with no Severity info. On this case, the Severity shall be listed as “UNDEFINED”
What’s an ecosystem?
An ecosystem is just the package deal supervisor, or sort of package deal. Examples embody rpm, npm, gems, and many others. Every supplier helps completely different ecosystems.
OSV
OSV is the default supplier for bomber. It’s an open, exact, and distributed method to producing and consuming vulnerability info for open supply.
You needn’t register for any service, get a password, or a token. Simply use bomber with out a supplier flag and away you go like this:
bomber scan check.cyclonedx.jsonSupported ecosystems
At the moment, the OSV helps the next ecosystems:
- Android
- crates.io
- Debian
- Go
- Maven
- NPM
- NuGet
- Packagist
- PyPI
- RubyGems
and others…
OSV Notes
The OSV supplier is fairly sluggish proper now when processing massive SBOMs. On the time of this writing, their batch endpoint just isn’t functioning, so bomber must name their API one package deal at a time.
Moreover, there are instances the place OSV doesn’t return a Severity, or a CVE/CWE. In these uncommon instances, bomber will output “UNSPECIFIED”, and “UNDEFINED” respectively.
Sonatype OSS Index
With the intention to use bomber with the Sonatype OSS Index you must get an account. Head over to the positioning, and create a free account, and make word of your username (this would be the electronic mail that you simply registered with).
When you log in, you will wish to navigate to your settings and make word of your API token. Please do not share your token with anybody.
Supported ecosystems
At the moment, the Sonatype OSS Index helps the next ecosystems:
- Maven
- NPM
- Go
- PyPi
- Nuget
- RubyGems
- Cargo
- CocoaPods
- Composer
- Conan
- Conda
- CRAN
- RPM
- Swift
Set up
Mac
You should utilize Homebrew to put in bomber utilizing the next:
brew faucet devops-kung-fu/homebrew-tap
brew set up devops-kung-fu/homebrew-tap/bomberFor those who shouldn’t have Homebrew, you possibly can nonetheless obtain the newest launch (ex: bomber_0.1.0_darwin_all.tar.gz), extract the recordsdata from the archive, and use the bomber binary.
If you want, you possibly can transfer the bomber binary to your /usr/native/bin listing or anyplace in your path.
Linux
To put in bomber, obtain the newest launch in your platform and set up domestically. For instance, set up bomber on Ubuntu:
dpkg -i bomber_0.1.0_linux_arm64.debUtilizing bomber
You may scan both a whole folder of SBOMs or a person SBOM with bomber. bomber would not care in case you have a number of codecs in a single folder. It will kind all the things out for you.
Observe that the default output for bomber is to STDOUT. Choices to output in HTML or JSON are described later on this doc.
Single SBOM scan
# Utilizing OSV (the default supplier) which doesn't require any credentials
bomber scan spdx.sbom.json# Utilizing a supplier that requires credentials (ossindex)
bomber scan --provider=xxx --username=xxx --token=xxx spdx-sbom.json
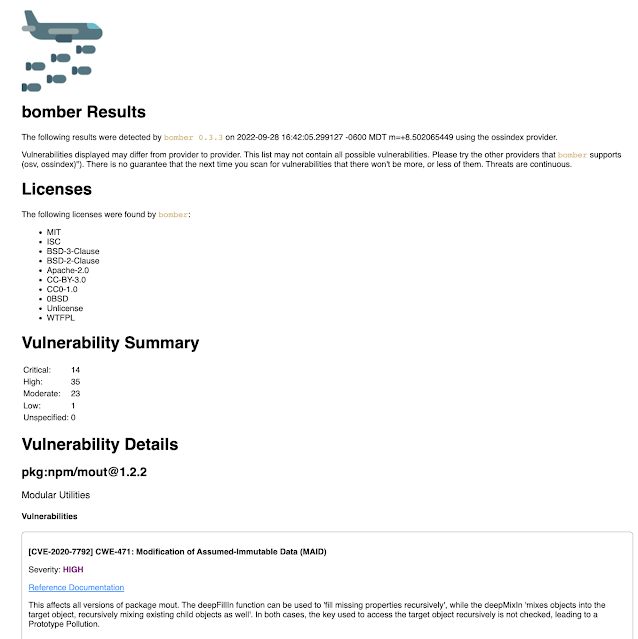
If the supplier finds vulnerabilities you will see an output just like the next:
If the supplier would not return any vulnerabilities you will see one thing like the next:
Complete folder scan
That is good for whenever you obtain a number of SBOMs from a vendor for a similar product. Or, possibly you wish to discover out what vulnerabilities you’ve gotten in your complete group. A folder scan will discover all parts, de-duplicate them, after which scan them for vulnerabilities.
# scan a folder of SBOMs (the next command will scan a folder in your present folder named "sboms")
bomber scan --username=xxx --token=xxx ./sbomsYou may see an analogous end result to what a Single SBOM scan will present.
Output to HTML
If you want a readable report generated with detailed vulnerability info, you possibly can utilized the --output flag to avoid wasting a report back to an HTML file.
Instance command:
bomber scan bad-bom.json --output=htmlThis may save a file in your present folder within the format “YYYY-MM-DD-HH-MM-SS-bomber-results.html”. For those who open this file in an internet browser, you will see output like the next:
Output to JSON
bomber can output vulnerability information in JSON format utilizing the --output flag. The default output is to STDOUT. There’s a ton of extra info within the JSON output than what will get displayed within the terminal. You can see a package deal description and what it is function is, what the vulnerability identify is, a abstract of the vulnerability, and extra.
Instance command:
bomber scan bad-bom.json --output=jsonSuperior stuff
If you want, you possibly can set two surroundings variables to retailer your credentials, and never need to sort them on the command line. Take a look at the Surroundings Variables info later on this README.
Surroundings Variables
For those who do not wish to enter credentials on a regular basis, you possibly can add the next to your .bashrc or .bash_profile
export BOMBER_PROVIDER_USERNAME={{your OSS Index consumer identify}}
export BOMBER_PROVIDER_TOKEN={{your OSS Index API Token}}Messing round
If you wish to kick the tires on bomber you will discover a collection of check SBOMs within the check folder.
Notes
- It is fairly uncommon to see SBOMs with license info. More often than not, the mills like Syft want a flag like
--license. For those who want license information, be sure to ask for it with the SBOM. - Hate to say it, however SPDX is wonky. If you do not get any outcomes on an SPDX file, attempt utilizing a CycloneDX file. On the whole you need to all the time attempt to get CycloneDX SBOMs out of your distributors.
- OSV. It is nice, however the API can be wonky. They’ve a batch endpoint that will make it a ton faster to get info again, but it surely would not work.
bombermust ship one PURL at a time to get vulnerabilities again, so in an enormous SBOM it’s going to take a while. We’ll regulate that. - OSV has one other concern the place the ecosystem would not all the time return vulnerabilities whenever you go it to their API. We needed to take away passing this to the API to get something to return. In addition they do not echo again the ecosystem so we won’t test to make sure that if we go one ecosystem to it, that we’re getting a vulnerability for a similar one again.
Contributing
If you want to contribute to the event of bomber please discuss with the CONTRIBUTING.md file on this repository. Please learn the CODE_OF_CONDUCT.md file earlier than contributing.
Software program Invoice of Supplies
bomber makes use of Syft to generate a Software program Invoice of Supplies each time a developer commits code to this repository (so long as Hookzis getting used and is has been initialized within the working listing). Extra info for CycloneDX is on the market right here.
The present CycloneDX SBOM for bomber is on the market right here.
Credit
An enormous thank-you to our associates at Smashicons for the bomber emblem.
Large kudos to our OSS homies at Sonatype for offering a depraved software just like the Sonatype OSS Index.