Dismember is a command-line toolkit for Linux that can be utilized to scan the reminiscence of all processes (or explicit ones) for frequent secrets and techniques and customized common expressions, amongst different issues.
It can finally change into a full /proc toolkit.
Utilizing the grep command, it could possibly match a common expression throughout all reminiscence for all (accessible) processes. This could possibly be used to search out delicate information in reminiscence, determine a course of by one thing included in its reminiscence, or to interrogate a processes’ reminiscence for attention-grabbing info.
There are numerous built-in patterns included by way of the scan command, which successfully works as a secret scanner towards the reminiscence in your machine.
Dismember can be utilized to go looking reminiscence of all processes it has entry to, so operating it as root is the simplest methodology.
Instructions are additionally included to listing processes, discover course of standing and associated info, draw course of bushes, and extra…
Predominant Instructions
| Command | Description |
|---|---|
grep |
Search course of reminiscence for a given string or regex |
scan |
Search course of reminiscence for a set of predefined secret patterns |
Utility Instructions
| Command | Description |
|---|---|
information |
Present a listing of information being accessed by a course of |
discover |
Discover a PID given a course of identify. If a number of processes match, the primary one is returned. |
data |
Present details about a course of |
kernel |
Present details about the kernel |
kill |
Kill a course of (or processes) utilizing SIGKILL |
listing |
Checklist all processes at the moment accessible on the system |
resume |
Resume a suspended course of utilizing SIGCONT |
droop |
Droop a course of utilizing SIGSTOP (use ‘dismember resume’ to depart suspension) |
tree |
Present a tree diagram of a course of and all youngsters (defaults to PID 1). |
Set up
Seize a binary from the newest launch and add it to your path.
Utilization Examples
Seek for a sample in a course of by PID
# search reminiscence owned by course of 1234
dismember grep -p 1234 'the password is .*'Seek for a sample in a course of by identify
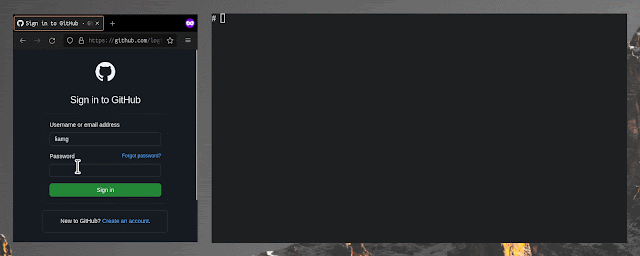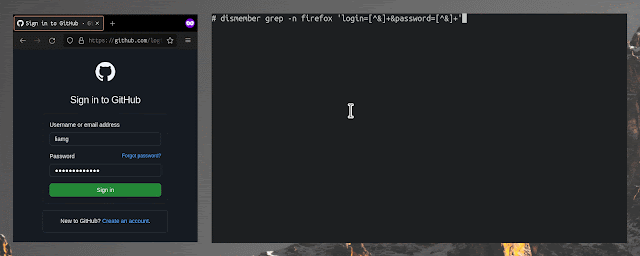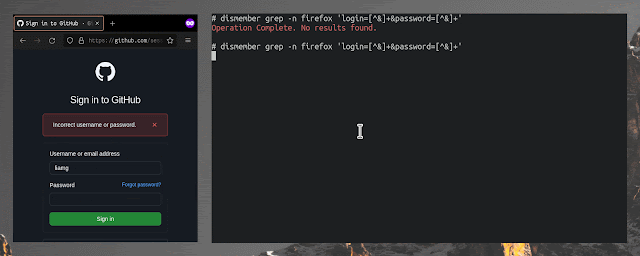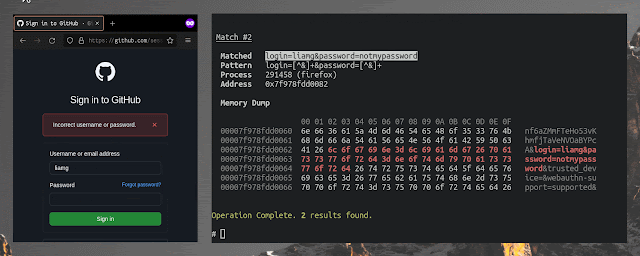
# search reminiscence owned by processes named "nginx" for a login kind submission
dismember grep -n nginx 'username=liamg&password=.*'Seek for a sample throughout all processes
# discover a github api token throughout all processes
dismember grep 'gh[pousr]_[0-9a-zA-Z]{36}'Seek for secrets and techniques in reminiscence throughout all processes
# search all accessible reminiscence for frequent secrets and techniques
dismember scanFAQ
Is not this info all simply sitting in
/proc?
Just about. Dismember simply reads and presents it for probably the most half. If you will get away with grep no matter /proc/[pid]/blah then go for it! I constructed this as an academic expertise as a result of I could not sleep one evening and stayed up late studying the proc man-pages (I reside a particularly rock ‘n’ roll life-style). It isn’t a substitute for present instruments, however maybe it could possibly complement them.
Have you learnt how horrific a few of these instructions appear when learn out of context?
Sure.