Traditionally, ransomware works by infecting a sufferer’s pc and encrypting all of the information with a key recognized solely by the menace actors behind the ransomware. With out this key, the sufferer can’t decrypt and skim any of the information on the pc. The menace actors then extort the sufferer by demanding cost in return for decrypting the information. Nevertheless, in more moderen years, ransomware has developed to facilitate a form of double extortion during which the menace actors each encrypt and exfiltrate victims’ information. Then, along with demanding a ransom for file decryption, the menace actors additionally threaten to publish the exfiltrated information on the web.
Growing ransomware that makes use of encryption could be tough. Menace actors are more and more turning into associates of ransomware builders and pay them a share of their income, reasonably than creating their very own ransomware. Nevertheless, encryption could be an unreliable ransomware method, as safety researchers can leverage bugs in ransomware to decrypt victims’ information. Inner disagreements between members of a ransomware gang also can drive members to leak the encryption key, as soon as once more giving safety researchers the flexibility to decrypt victims’ information.
Ransomware double extortion is normally aided by a devoted leak website (DLS) on the Tor community the place menace actors publish each their threats and victims’ information, within the occasion that the victims don’t pay the ransom. These devoted leak websites are run by ransomware gangs that function in accordance with the ransomware-as-a-service (RaaS) mannequin. These gangs develop ransomware and distribute it to varied affiliate actors, who in flip use this software program to encrypt and exfiltrate victims’ information. The associates then should pay a share of all ransom income to the gang that develops the ransomware and publicizes double extortion threats to its DLS.
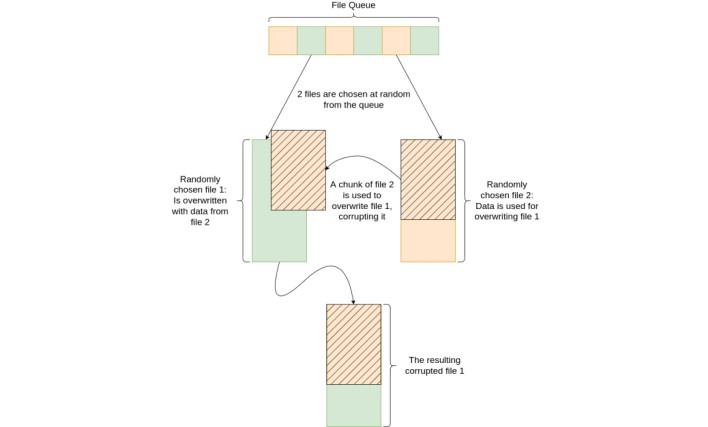
Not like encryption, this corruption course of doesn’t use a key that would reverse the method, that means the corrupted information are rendered completely unreadable. This type of information corruption proves advantageous for the ransomware affiliate actors whose exfiltrated copy of the information stays uncorrupted. Fairly than providing to decrypt information on victims’ computer systems for a value, the menace actors can as an alternative extort victims by charging victims a ransom payment for the possibility to obtain the uncorrupted copies of their information from the menace actors.
If ransomware have been to shift to from information encryption to information corruption, menace actors wouldn’t have to fret about safety researchers decrypting victims’ information. Moreover, menace actors might use widespread information exfiltration and corruption instruments at no cost, reasonably than paying a share of their income to ransomware builders. These benefits could drive menace actors towards corruption over encryption as a ransomware method. That mentioned, cybersecurity researchers have to this point noticed just one occasion of corruption used instead of encryption, so now we have but to see whether or not this substitution turns into a development.


