Russian state-sponsored actors are persevering with to strike Ukrainian entities with information-stealing malware as a part of what’s suspected to be an espionage operation.
Symantec, a division of Broadcom Software program, attributed the malicious marketing campaign to a menace actor tracked Shuckworm, also referred to as Actinium, Armageddon, Gamaredon, Primitive Bear, and Trident Ursa. The findings have been corroborated by the Pc Emergency Response Crew of Ukraine (CERT-UA).
The menace actor, lively since a minimum of 2013, is thought for explicitly singling out private and non-private entities in Ukraine. The assaults have since ratcheted up within the wake of Russia’s army invasion in late 2022.
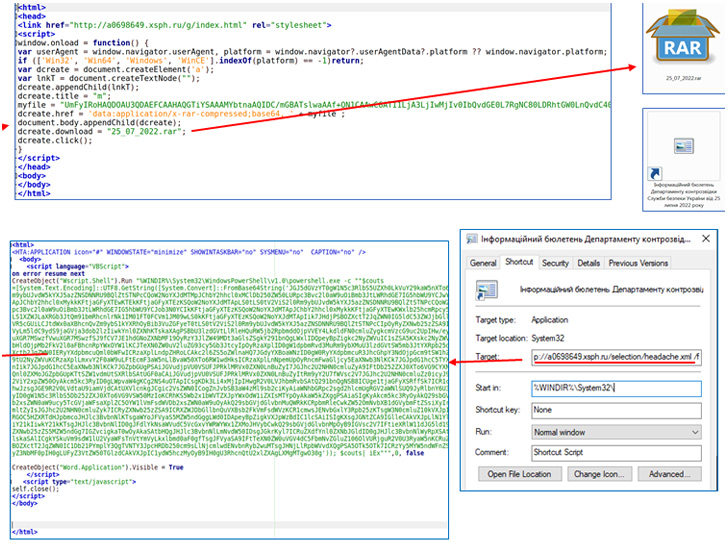
The newest set of assaults are mentioned to have commenced on July 15, 2022, and ongoing as lately as August 8, with the an infection chains leveraging phishing emails disguised as newsletters and fight orders, in the end resulting in the deployment of a PowerShell stealer malware dubbed GammaLoad.PS1_v2.
Additionally delivered to the compromised machines are two backdoors named Giddome and Pterodo, each of that are trademark Shuckworm instruments which were regularly redeveloped by the attackers in a bid to remain forward of detection.
At its core, Pterodo is a Visible Primary Script (VBS) dropper malware with capabilities to execute PowerShell scripts, use scheduled duties (shtasks.exe) to keep up persistence, and obtain extra code from a command-and-control server.
The Giddome implant, however, options a number of capabilities, together with recording audio, capturing screenshots, logging keystrokes, and retrieving and executing arbitrary executables onto the contaminated hosts.
The intrusions, which happen by emails distributed from compromised accounts, additional leverage official software program like Ammyy Admin and AnyDesk to facilitate distant entry.
The findings come because the Gamaredon actor has been linked to a collection of social engineering assaults aimed toward initiating the GammaLoad.PS1 supply chain, enabling the menace actor to steal recordsdata and credentials saved in internet browsers.
“Because the Russian invasion of Ukraine approaches the six-month mark, Shuckworm’s long-time deal with the nation seems to be persevering with unabated,” Symantec famous.
“Whereas Shuckworm just isn’t essentially essentially the most tactically subtle espionage group, it compensates for this in its focus and persistence in relentlessly focusing on Ukrainian organizations.”
The findings comply with an alert from CERT-UA, which cautioned of “systematic, huge and geographically dispersed” phishing assaults involving the usage of a .NET downloader known as RelicRace to execute payloads similar to Formbook and Snake Keylogger.