A menace cluster linked to the Russian nation-state actor tracked as Sandworm has continued its concentrating on of Ukraine with commodity malware by masquerading as telecom suppliers, new findings present.
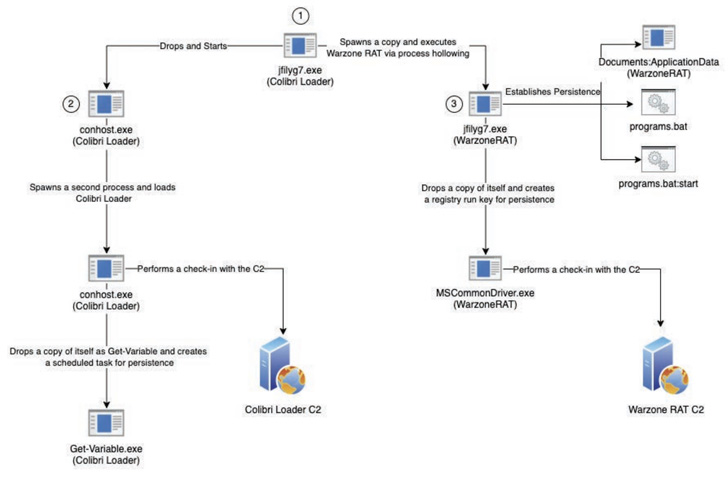
Recorded Future mentioned it found new infrastructure belonging to UAC-0113 that mimics operators like Datagroup and EuroTransTelecom to ship payloads similar to Colibri loader and Warzone RAT.
The assaults are mentioned to be an enlargement of the similar marketing campaign that beforehand distributed DCRat (or DarkCrystal RAT) utilizing phishing emails with authorized aid-themed lures in opposition to suppliers of telecommunications in Ukraine.
Sandworm is a damaging Russian menace group that is finest identified for finishing up assaults such because the 2015 and 2016 concentrating on of Ukrainian electrical grid and 2017’s NotPetya assaults. It is confirmed to be Unit 74455 of Russia’s GRU army intelligence company.
The adversarial collective, often known as Voodoo Bear, sought to break high-voltage electrical substations, computer systems and networking tools for the third time in Ukraine earlier this April by means of a new variant of a chunk of malware generally known as Industroyer.
Russia’s invasion of Ukraine has additionally had the group unleash quite a few different assaults, together with leveraging the Follina vulnerability (CVE-2022-30190) within the Microsoft Home windows Help Diagnostic Instrument (MSDT) to breach media entities within the Japanese European nation.
As well as, it was uncovered because the mastermind behind a brand new modular botnet referred to as Cyclops Blink that enslaved internet-connected firewall gadgets and routers from WatchGuard and ASUS.
The U.S. authorities, for its half, has introduced as much as $10 million in rewards for data on six hackers related to the APT group for taking part in malicious cyber actions in opposition to crucial infrastructure within the nation.
“A transition from DarkCrystal RAT to Colibri Loader and Warzone RAT demonstrates UAC-0113’s broadening however persevering with use of publicly out there commodity malware,” Recorded Future mentioned.
The assaults entail the fraudulent domains internet hosting an internet web page purportedly about “Odesa Regional Army Administration,” whereas an encoded ISO picture payload is stealthily deployed by way of a method known as HTML smuggling.
HTML smuggling, because the identify goes, is an evasive malware supply approach that leverages official HTML and JavaScript options to distribute malware and get round typical safety controls.
Recorded Future additionally mentioned it recognized factors of similarities with one other HTML dropper attachment put to make use of by the APT29 menace actor in a marketing campaign geared toward Western diplomatic missions between Could and June 2022.
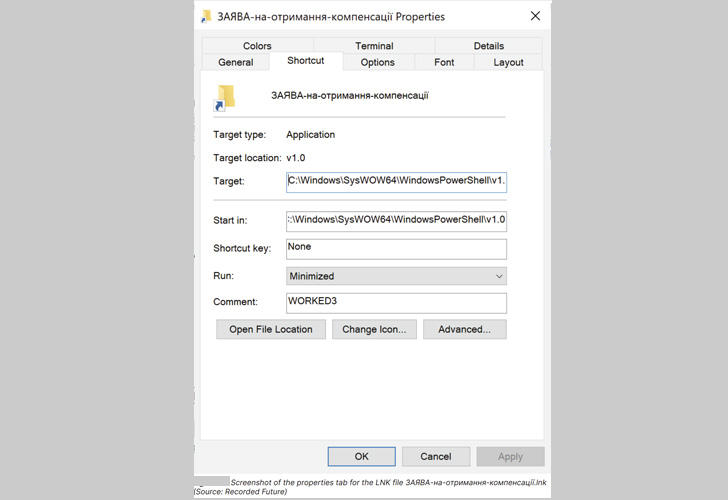
Embedded throughout the ISO file, which was created on August 5, 2022, are three recordsdata, together with an LNK file that tips the sufferer into activating the an infection sequence, ensuing within the deployment of each Colibri loader and Warzone RAT to the goal machine.
The execution of the LNK file additionally launches an innocuous decoy doc – an utility for Ukrainian residents to request for financial compensation and gasoline reductions – in an try to hide the malicious operations.