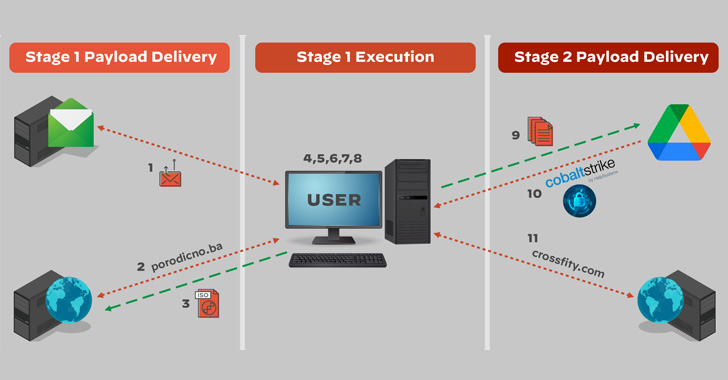
The Russian state-sponsored hacking collective generally known as APT29 has been attributed to a brand new phishing marketing campaign that takes benefit of professional cloud providers like Google Drive and Dropbox to ship malicious payloads on compromised programs.
“These campaigns are believed to have focused a number of Western diplomatic missions between Might and June 2022,” Palo Alto Networks Unit 42 mentioned in a Tuesday report. “The lures included in these campaigns counsel focusing on of a overseas embassy in Portugal in addition to a overseas embassy in Brazil.”
APT29, additionally tracked beneath the monikers Cozy Bear, Cloaked Ursa, or The Dukes, has been characterised as an organized cyberespionage group working to gather intelligence that aligns with Russia’s strategic targets.
Some features of the superior persistent risk’s actions, together with the notorious SolarWinds provide chain assault of 2020, are individually tracked by Microsoft beneath the identify Nobelium, with Mandiant calling it an evolving, disciplined, and extremely expert risk actor that operates with a heightened degree of operational safety.”
The latest intrusions are a continuation of the identical covert operation beforehand detailed by Mandiant and Cluster25 in Might 2022, wherein the spear-phishing emails led to the deployment of Cobalt Strike Beacons by way of an HTML dropper attachment dubbed EnvyScout (aka ROOTSAW) hooked up on to the missives.
What’s modified within the newer iterations is the usage of cloud providers like Dropbox and Google Drive to hide their actions and retrieve extra malware into goal environments. A second model of the assault noticed in late Might 2022 is alleged to have tailored additional to host the HTML dropper in Dropbox.
“The campaigns and the payloads analyzed over time present a powerful concentrate on working beneath the radar and reducing the detection charges,” Cluster25 famous on the time. “On this regard, even the usage of professional providers resembling Trello and Dropbox counsel the adversary’s will to function for a very long time throughout the sufferer environments remaining undetected.”
EnvyScout, for its half, serves as an auxiliary instrument to additional infect the goal with the actor’s implant of selection, on this case, a .NET-based executable that is hid in a number of layers of obfuscation and used to exfiltrate system data in addition to execute next-stage binaries resembling Cobalt Strike fetched from Google Drive.
“The usage of DropBox and Google Drive providers […] is a brand new tactic for this actor and one which proves difficult to detect as a result of ubiquitous nature of those providers and the truth that they’re trusted by thousands and thousands of shoppers worldwide,” the researchers mentioned.
The findings additionally coincide with a brand new declaration from the Council of the European Union, calling out the spike in malicious cyber actions perpetrated by Russian risk actors and “condemn[ing] this unacceptable habits in our on-line world.”
“This improve in malicious cyber actions, within the context of the battle towards Ukraine, creates unacceptable dangers of spillover results, misinterpretation and potential escalation,” the Council mentioned in a press assertion.