Russian menace actors capitalized on the ongoing battle in opposition to Ukraine to distribute Android malware camouflaged as an app for pro-Ukrainian hacktivists to launch distributed denial-of-service (DDoS) assaults in opposition to Russian websites.
Google Risk Evaluation Group (TAG) attributed the malware to Turla, a sophisticated persistent menace often known as Krypton, Venomous Bear, Waterbug, and Uroburos, and linked to Russia’s Federal Safety Service (FSB).
“That is the primary identified occasion of Turla distributing Android-related malware,” TAG researcher Billy Leonard stated. “The apps weren’t distributed by means of the Google Play Retailer, however hosted on a website managed by the actor and disseminated through hyperlinks on third occasion messaging providers.”
It is price noting that the onslaught of cyberattacks within the rapid aftermath of Russia’s unprovoked invasion of Ukraine prompted the latter to kind an IT Military to stage counter-DDoS assaults in opposition to Russian web sites. The purpose of the Turla operation, it seems, is to make use of this volunteer-run effort to their very own benefit.
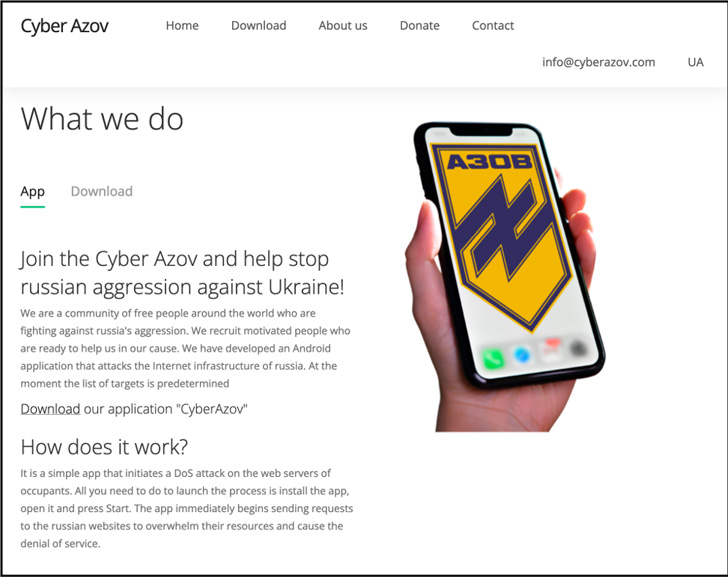
The decoy app was hosted on a website masquerading because the Azov Regiment, a unit of the Nationwide Guard of Ukraine, calling on individuals from all over the world to combat “Russia’s aggression” by initiating a denial-of-service assault on the internet servers belonging to “Russian web sites to overwhelm their assets.”
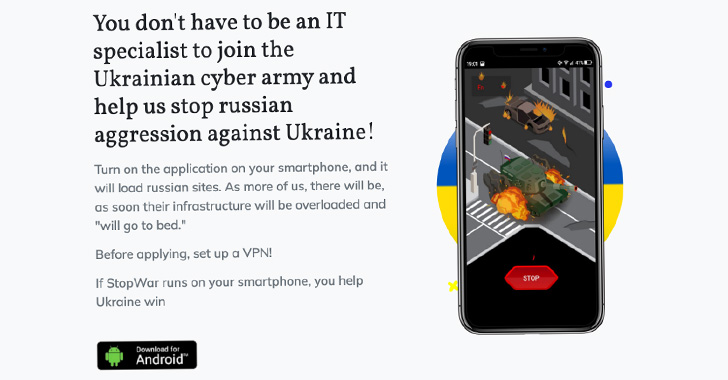
Google TAG stated the actors drew inspiration from one other Android app distributed by means of a web site named “stopwar[.]professional” that is additionally designed to conduct DoS assaults by regularly sending requests to the goal web sites.
That stated, the precise variety of instances the malicious Cyber Azov app was put in is minuscule, posing no main influence on Android customers.
Moreover, the Sandworm group (aka Voodoo Bear) has been related to a separate set of malicious actions leveraging the Follina vulnerability (CVE-2022-30190) within the Microsoft Home windows Help Diagnostic Software (MSDT) to ship hyperlinks pointing to Microsoft Workplace paperwork hosted on compromised web sites focusing on media entities in Ukraine.
UAC-0098, a menace actor that CERT-UA final month warned of distributing tax-themed paperwork carrying a Follina exploit, has additionally been assessed to be a former preliminary entry dealer with ties to the Conti group in command of disseminating the IcedID banking trojan.
Other forms of cyber exercise embody credential phishing assaults mounted by an adversary known as COLDRIVER (aka Callisto) geared toward authorities and protection officers, politicians, NGOs and suppose tanks, and journalists.
These contain sending emails both instantly, together with the phishing area or containing hyperlinks to paperwork hosted on Google Drive and Microsoft OneDrive that, in flip, function hyperlinks to an attacker-controlled web site designed to steal passwords.
The newest developments are yet one more indication of how Russian menace actors are exhibiting continued indicators of accelerating sophistication of their makes an attempt to focus on in ways in which spotlight their evolving methods.