A state-sponsored hacking group with hyperlinks to Russia has been linked to assault infrastructure that spoofs the Microsoft login web page of World Ordnance, a professional U.S.-based army weapons and {hardware} provider.
Recorded Future attributed the brand new infrastructure to a risk exercise group it tracks underneath the title TAG-53, and is broadly identified by the cybersecurity group as Callisto, COLDRIVER, SEABORGIUM, and TA446.
“Based mostly on historic public reporting on overlapping TAG-53 campaigns, it’s seemingly that this credential harvesting exercise is enabled partly via phishing,” Recorded Future’s Insikt Group mentioned in a report revealed this week.
The cybersecurity agency mentioned it found 38 domains, 9 of which contained references to corporations like UMO Poland, Sangrail LTD, DTGruelle, Blue Sky Community, the Fee for Worldwide Justice and Accountability (CIJA), and the Russian Ministry of Inner Affairs.
It is suspected that the themed domains are seemingly an try on a part of the adversary to masquerade as genuine events in social engineering campaigns.
“Notably, a constant development has emerged concerning using particularly tailor-made infrastructure by TAG-53 highlighting the long-term use of comparable strategies for his or her strategic campaigns,” the researchers mentioned.
The event comes practically 4 months after Microsoft disclosed that it took steps to disrupt phishing and credential theft assaults mounted by the group with the aim of breaching protection and intelligence consulting corporations in addition to NGOs, assume tanks, and better training entities within the U.Okay. and the U.S.
Enterprise safety firm Proofpoint has additional known as out the group for its subtle impersonation ways to ship rogue phishing hyperlinks.
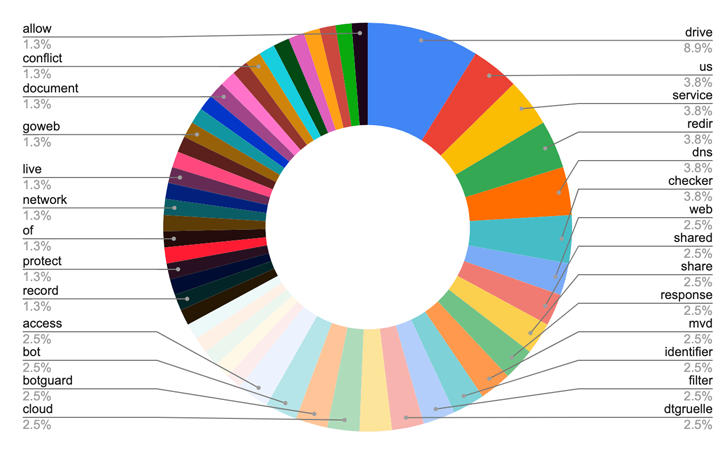 |
| Phrases utilized in TAG-53 linked domains |
Moreover, the risk actor has been attributed with low confidence to a spear-phishing operation concentrating on Ukraine’s Ministry of Defence coinciding with the onset of Russia’s army invasion of the nation earlier this March.
SEKOIA.IO, in a separate write-up, corroborated the findings, uncovering a complete of 87 domains, with two of them alluding to personal sector corporations Emcompass and BotGuard. Additionally focused have been 4 NGOs concerned in Ukraine disaster aid.
A kind of assaults concerned e-mail communications between the NGO and the attacker utilizing a spoofed e-mail deal with mimicking a trusted supply, adopted by sending a malicious PDF containing a phishing hyperlink in an try and evade detection from e-mail gateways.
“The e-mail alternate exhibits that the attacker didn’t embrace the malicious payload within the first e-mail, however waited to get a solution to construct a relationship and keep away from suspicion earlier than sending the payload to the sufferer,” the cybersecurity firm defined.
Using typosquatted Russian ministry domains additional provides weight to Microsoft’s evaluation that SEABORGIUM targets former intelligence officers, consultants in Russian affairs, and Russian residents overseas.
SEKOIA.IO additionally characterised the concentrating on of CIJA as an intelligence gathering mission designed to amass “battle crime-related proof and/or worldwide justice procedures, prone to anticipate and construct counter narrative on future accusations.”
The disclosures arrive as risk intelligence agency Lupovis revealed that Russian risk actors have compromised the networks belonging to a number of corporations within the U.Okay., the U.S., France, Brazil, South Africa, and are “rerouting via their networks” to launch assaults in opposition to Ukraine.
Microsoft, in the mean time, has warned of “potential Russian assault within the digital area over the course of this winter,” stating Moscow’s “multi-pronged hybrid expertise strategy” of conducting cyber strikes in opposition to civilian infrastructure and affect operations searching for to gas discord in Europe.