The Russia-linked Gamaredon group tried to unsuccessfully break into a big petroleum refining firm inside a NATO member state earlier this yr amid the continued Russo-Ukrainian warfare.
The assault, which befell on August 30, 2022, is only one of a number of assaults orchestrated by the superior persistent menace (APT) that is attributed to Russia’s Federal Safety Service (FSB).
Gamaredon, additionally recognized by the monikers Actinium, Armageddon, Iron Tilden, Primitive Bear, Shuckworm, Trident Ursa, and Winterflounder, has a historical past of primarily going after Ukrainian entities and, to a lesser extent, NATO allies to reap delicate knowledge.
“Because the battle has continued on the bottom and in our on-line world, Trident Ursa has been working as a devoted entry creator and intelligence gatherer,” Palo Alto Networks Unit 42 mentioned in a report shared with The Hacker Information. “Trident Ursa stays one of the vital pervasive, intrusive, constantly energetic and centered APTs focusing on Ukraine.”
Unit 42’s continued monitoring of the group’s actions has uncovered greater than 500 new domains, 200 malware samples, and a number of shifts in its techniques over the previous 10 months in response to ever-changing and increasing priorities.
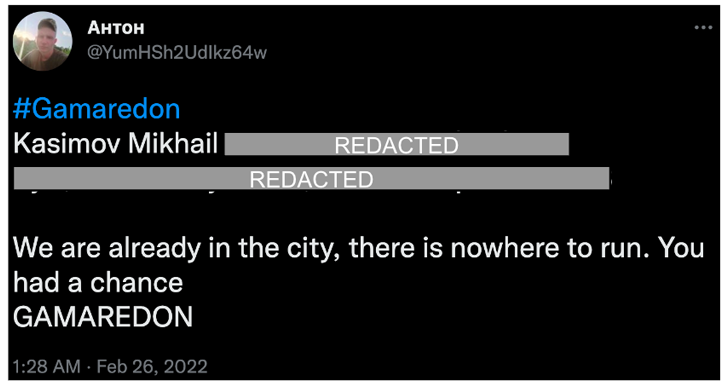
Past cyberattacks, the bigger safety group is alleged to have been on the receiving finish of threatening tweets from a purported Gamaredon affiliate, highlighting the intimidation strategies adopted by the adversary.
Different noteworthy strategies embody the usage of Telegram pages to lookup command-and-control (C2) servers and quick flux DNS to rotate via many IP addresses in a brief span of time to make IP-based denylisting and takedown efforts tougher.
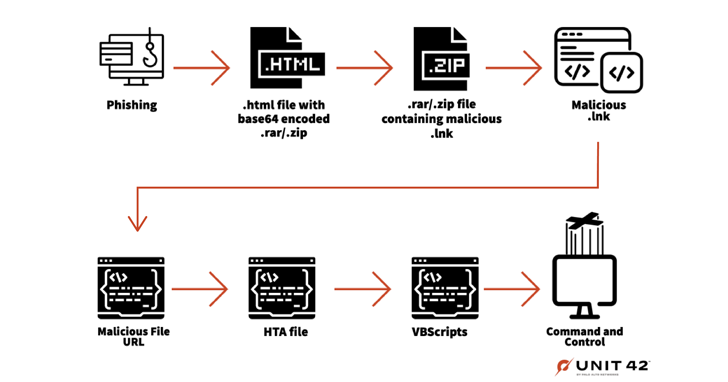
The assaults themselves entail the supply of weaponized attachments embedded inside spear-phishing emails to deploy a VBScript backdoor on the compromised host that is able to establishing persistence and executing further VBScript code equipped by the C2 server.
Gamaredon an infection chains have additionally been noticed leveraging geoblocking to restrict the assaults to particular places together with using dropper executables to launch next-stage VBScript payloads, which subsequently connect with the C2 server to execute additional instructions.
The geoblocking mechanism capabilities as a safety blindspot because it reduces the visibility of the menace actor’s assaults exterior of the focused international locations and makes its actions tougher to trace.
“Trident Ursa stays an agile and adaptive APT that doesn’t use overly refined or advanced strategies in its operations,” the researchers mentioned. “Typically, they depend on publicly obtainable instruments and scripts – together with a big quantity of obfuscation – in addition to routine phishing makes an attempt to efficiently execute their operations.”