An ongoing espionage marketing campaign operated by the Russia-linked Gamaredon group is focusing on staff of Ukrainian authorities, protection, and legislation enforcement companies with a bit of custom-made data stealing malware.
“The adversary is utilizing phishing paperwork containing lures associated to the Russian invasion of Ukraine,” Cisco Talos researchers Asheer Malhotra and Guilherme Venere mentioned in a technical write-up shared with The Hacker Information. “LNK recordsdata, PowerShell, and VBScript allow preliminary entry, whereas malicious binaries are deployed within the post-infection part.”
Energetic since 2013, Gamaredon – also referred to as Actinium, Armageddon, Primitive Bear, Shuckworm, and Trident Ursa – has been linked to quite a few assaults aimed toward Ukrainian entities within the aftermath of Russia’s navy invasion of Ukraine in late February 2022.
The focused phishing operation, noticed as not too long ago as August 2022, additionally follows related intrusions uncovered by Symantec final month involving using malware similar to Giddome and Pterodo. The first objective of those assaults is to determine long-term entry for espionage and information theft.
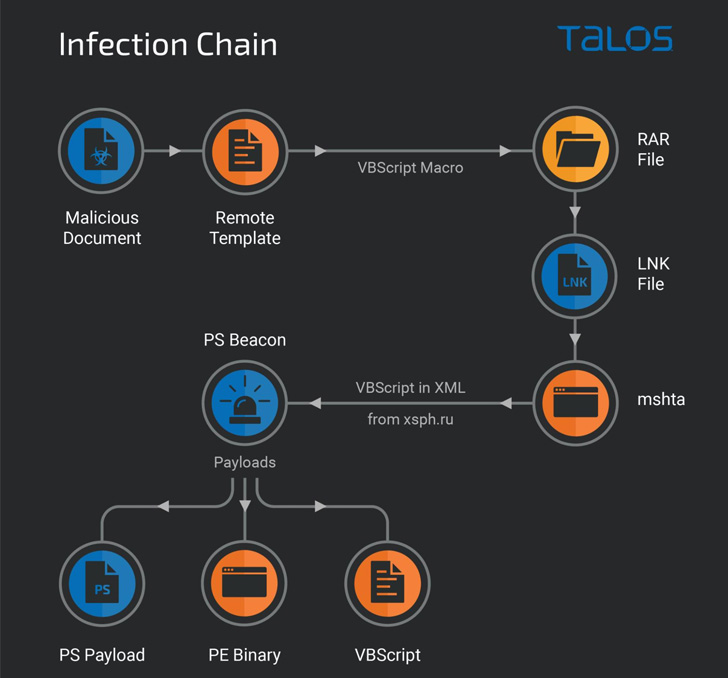
It entails leveraging decoy Microsoft Phrase paperwork containing lures associated to the Russian invasion of Ukraine distributed through electronic mail messages to contaminate targets. When opened, macros hid inside distant templates are executed to retrieve RAR containing LNK recordsdata.
The LNK recordsdata seemingly reference intelligence briefings associated to the Russian invasion of Ukraine to trick unsuspecting victims into opening the shortcuts, ensuing within the execution of a PowerShell beacon script that in the end paves the best way for next-stage payloads.
This contains one other PowerShell script that is used to offer persistent entry to compromised system and ship further malware, together with a brand new malware able to plundering recordsdata (.doc, .docx, .xls, .rtf, .odt, .txt, .jpg, .jpeg, .pdf, .ps1, .rar, .zip, .7z, and .mdb) from the machine in addition to any detachable drive linked to it.
“The infostealer is a dual-purpose malware that features capabilities for exfiltrating particular file varieties and deploying further binary and script-based payloads on an contaminated endpoint,” the researchers mentioned, including it could be a element of the Giddome backdoor household.
The findings come at a time cyberattacks proceed to be an necessary a part of fashionable hybrid battle technique amidst the battle between Russia and Ukraine. Earlier this month, Google’s Menace Evaluation Group (TAG) disclosed as many as 5 totally different campaigns mounted by a bunch with hyperlinks to the Conti cybercrime cartel.