Researchers have disclosed a number of vulnerabilities impacting Extremely-wideband (UWB) Actual-time Finding Techniques (RTLS), enabling risk actors to launch adversary-in-the-middle (AitM) assaults and tamper with location information.
“The zero-days discovered particularly pose a safety danger for staff in industrial environments,” cybersecurity agency Nozomi Networks disclosed in a technical write-up final week. “If a risk actor exploits these vulnerabilities, they’ve the power to tamper with security zones designated by RTLS to guard staff in hazardous areas.”
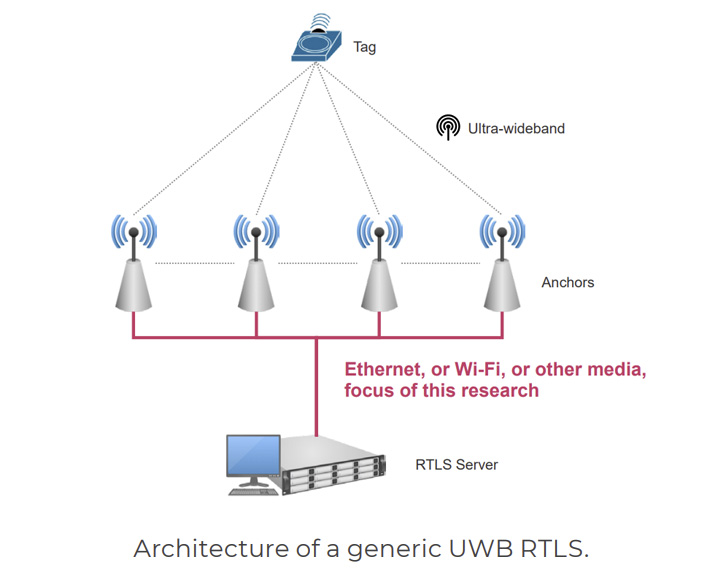
RTLS is used to robotically establish and monitor the situation of objects or folks in real-time, often inside a confined indoor space. That is achieved by making use of tags which might be hooked up to belongings, which broadcast USB alerts to mounted reference factors known as anchors that then decide their location.
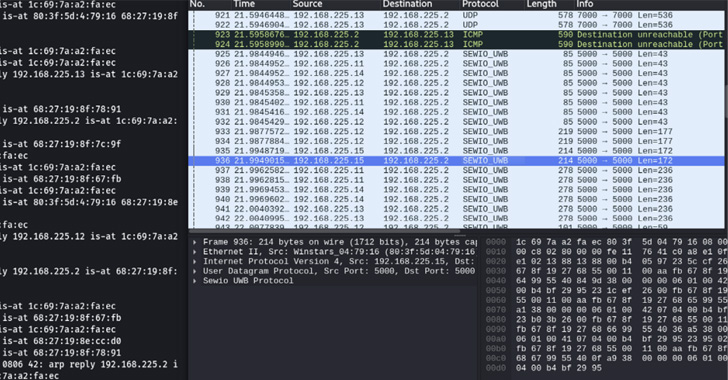
However flaws recognized in RTLS options – Sewio Indoor Monitoring RTLS UWB Wi-Fi Equipmenta and Avalue Renity Artemis Enterprise Equipment – meant that they might be weaponized to intercept community packets exchanged between anchors and the central server and stage visitors manipulation assaults.
Put merely, the concept is to estimate the anchor coordinates and use it to govern the geofencing guidelines of the RTLS system, successfully tricking the software program into granting entry to restricted areas and even inflicting disruption to manufacturing environments.
“If an attacker is ready to alter the place of a tag by modifying the positioning packet associated to that tag, it could grow to be attainable to enter restricted zones or steal helpful gadgets with out the operators with the ability to detect {that a} malicious exercise is ongoing.”
Even worse, by altering the place of tags and putting them inside areas monitored by geofencing guidelines, an adversary may cause the stoppage of total manufacturing traces by exhibiting {that a} employee is close by even when nobody is definitely round.
In an alternate situation, the situation information might be tampered to put a employee exterior of a geofencing zone in order that harmful equipment would restart whereas a employee is in shut proximity, posing extreme security dangers.
However it’s value stating that doing so necessitates that an attacker both compromises a pc linked to that community, or surreptitiously provides a rogue system to achieve unauthorized entry to the community.
To remediate such assaults, it is really helpful to implement community segregation and add a visitors encryption layer on high of the prevailing communications to forestall AitM assaults.
“Weak safety necessities in crucial software program can result in issues of safety that can not be ignored,” researchers Andrea Palanca, Luca Cremona, and Roya Gordon stated. “Exploiting secondary communications in UWB RTLS will be difficult, however it’s doable.”