The cell risk marketing campaign tracked as Roaming Mantis has been linked to a brand new wave of compromises directed towards French cell phone customers, months after it expanded its focusing on to incorporate European nations.
No fewer than 70,000 Android units are mentioned to have been contaminated as a part of the lively malware operation, Sekoia mentioned in a report printed final week.
Assault chains involving Roaming Mantis, a financially motivated Chinese language risk actor, are recognized to both deploy a bit of banking trojan named MoqHao (aka XLoader) or redirect iPhone customers to credential harvesting touchdown pages that mimic the iCloud login web page.
“MoqHao (aka Wroba, XLoader for Android) is an Android distant entry trojan (RAT) with information-stealing and backdoor capabilities that possible spreads by way of SMS,” Sekoia researchers mentioned.
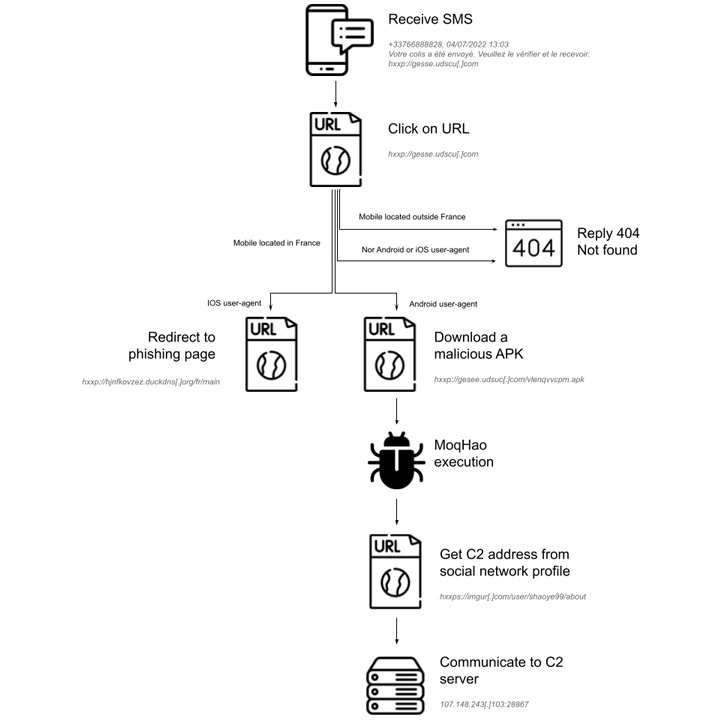
All of it begins with a phishing SMS, a method generally known as smishing, attractive customers with bundle delivery-themed messages containing rogue hyperlinks, that, when clicked, proceed to obtain the malicious APK file, however solely after figuring out if a sufferer’s location is inside French borders.
Ought to a recipient be positioned exterior France and the gadget working system is neither Android nor iOS – an element ascertained by checking the IP tackle and the Person-Agent string – the server is designed to reply with a “404 Not discovered” standing code.
“The smishing marketing campaign is subsequently geofenced and goals to put in Android malware, or accumulate Apple iCloud credentials,” the researchers identified.
MoqHao sometimes makes use of domains generated via the dynamic DNS service Duck DNS for its first-stage supply infrastructure. What’s extra, the malicious app masquerades because the Chrome internet browser utility to trick customers into granting it invasive permissions.
The spyware and adware trojan offers a pathway window for distant interplay with the contaminated units, enabling the adversary to stealthily harvest delicate knowledge similar to iCloud knowledge, contact lists, name historical past, SMS messages, amongst others.
Sekoia additionally assessed that the amassed knowledge might be used to facilitate extortion schemes and even bought to different risk actors for revenue. “greater than 90.000 distinctive IP addresses that requested the C2 server distributing MoqHao,” the researchers famous.