This repository is a documentation of my adventures with Stratus Purple Group – a device for adversary emulation for the cloud.
Stratus Purple Group is “Atomic Purple Group for the cloud, permitting to emulate offensive assault methods in a granular and self-contained method.
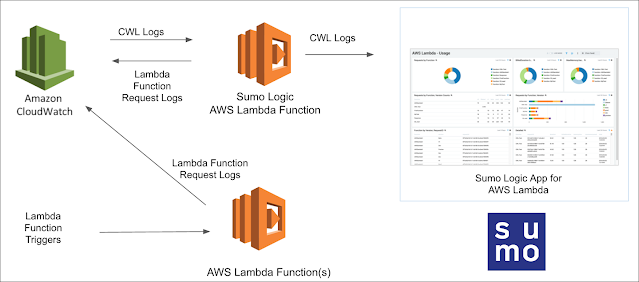
We run the assaults coated within the Stratus Purple Group repository one after the other on our AWS account. As a way to monitor them, we’ll use CloudTrail and CloudWatch for logging and ingest these logs into SumoLogic for additional evaluation.
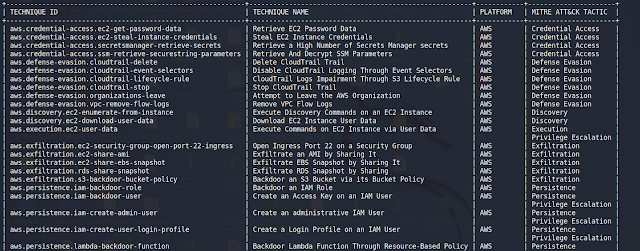
| Assault | Description | Hyperlink |
|---|---|---|
| aws.credential-access.ec2-get-password-data | Retrieve EC2 Password Knowledge | Hyperlink |
| aws.credential-access.ec2-steal-instance-credentials | Steal EC2 Occasion Credentials | Hyperlink |
| aws.credential-access.secretsmanager-retrieve-secrets | Retrieve a Excessive Variety of Secrets and techniques Supervisor secrets and techniques | Hyperlink |
| aws.credential-access.ssm-retrieve-securestring-parameters | Retrieve And Decrypt SSM Parameters | Hyperlink |
| aws.defense-evasion.cloudtrail-delete | Delete CloudTrail Path | Hyperlink |
| aws.defense-evasion.cloudtrail-event-selectors | Disable CloudTrail Logging By Occasion Selectors | Hyperlink |
| aws.defense-evasion.cloudtrail-lifecycle-rule | CloudTrail Logs Impairment By S3 Lifecycle Rule | Hyperlink |
| aws.defense-evasion.cloudtrail-stop | Cease CloudTrail Path | Hyperlink |
| aws.defense-evasion.organizations-leave | Try and Depart the AWS Group | Hyperlink |
| aws.defense-evasion.vpc-remove-flow-logs | Take away VPC Stream Logs | Hyperlink |
| aws.discovery.ec2-enumerate-from-instance | Execute Discovery Instructions on an EC2 Occasion | Hyperlink |
| aws.discovery.ec2-download-user-data | Obtain EC2 Occasion Person Knowledge | TBD |
| aws.exfiltration.ec2-security-group-open-port-22-ingress | Open Ingress Port 22 on a Safety Group | Hyperlink |
| aws.exfiltration.ec2-share-ami | Exfiltrate an AMI by Sharing It | Hyperlink |
| aws.exfiltration.ec2-share-ebs-snapshot | Exfiltrate EBS Snapshot by Sharing It | Hyperlink |
| aws.exfiltration.rds-share-snapshot | Exfiltrate RDS Snapshot by Sharing | Hyperlink |
| aws.exfiltration.s3-backdoor-bucket-policy | Backdoor an S3 Bucket through its Bucket Coverage | Hyperlink |
| aws.persistence.iam-backdoor-role | Backdoor an IAM Function | Hyperlink |
| aws.persistence.iam-backdoor-user | Create an Entry Key on an IAM Person | TBD |
| aws.persistence.iam-create-admin-user | Create an administrative IAM Person | TBD |
| aws.persistence.iam-create-user-login-profile | Create a Login Profile on an IAM Person | TBD |
| aws.persistence.lambda-backdoor-function | Backdoor Lambda Perform By Useful resource-Based mostly Coverage | TBD |
Credit
- Superior group at Datadog, Inc. for Stratus Purple Group right here
- Hacking the Cloud AWS
- Falcon Power group weblog