A brand new, large-scale phishing marketing campaign has been noticed utilizing adversary-in-the-middle (AitM) methods to get round safety protections and compromise enterprise e mail accounts.
“It makes use of an adversary-in-the-middle (AitM) assault method able to bypassing multi-factor authentication,” Zscaler researchers Sudeep Singh and Jagadeeswar Ramanukolanu stated in a Tuesday report. “The marketing campaign is particularly designed to achieve finish customers in enterprises that use Microsoft’s e mail companies.”
Distinguished targets embrace fintech, lending, insurance coverage, power, manufacturing, and federal credit score union verticals positioned within the U.S., U.Ok., New Zealand, and Australia.
This isn’t the primary time such a phishing assault has come to mild. Final month, Microsoft disclosed that over 10,000 organizations had been focused since September 2021 via AitM methods to breach accounts secured with multi-factor authentication (MFA).
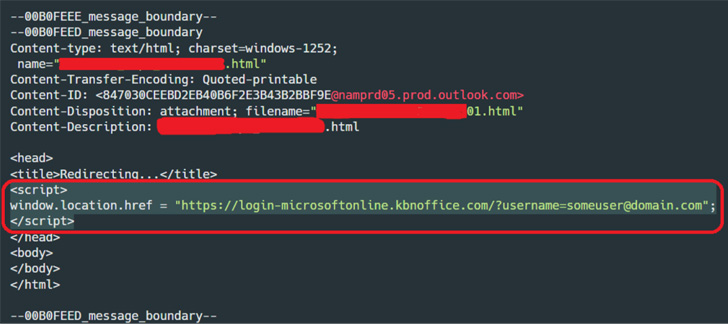
The continuing marketing campaign, efficient June 2022, commences with an invoice-themed e mail despatched to targets containing an HTML attachment, which features a phishing URL embedded inside it.
Opening the attachment through an internet browser redirects the e-mail recipient to the phishing web page that masquerades as a login web page for Microsoft Workplace, however not earlier than fingerprinting the compromised machine to find out whether or not the sufferer is definitely the supposed goal.
AitM phishing assaults transcend the standard phishing approaches designed to plunder credentials from unwitting customers, notably in eventualities the place MFA is enabled – a safety barrier that stops the attacker from logging into the account with solely the stolen credentials.
To avoid this, the rogue touchdown web page developed utilizing a phishing package capabilities as a proxy that captures and relays all of the communication between the consumer (i.e., sufferer) and the e-mail server.
“The kits intercept the HTML content material obtained from the Microsoft servers, and earlier than relaying it again to the sufferer, the content material is manipulated by the package in varied methods as wanted, to ensure the phishing course of works,” the researchers stated.
This additionally entails changing all of the hyperlinks to the Microsoft domains with equal hyperlinks to the phishing area in order to make sure that the back-and-forth stays intact with the fraudulent web site all through the session.
Zscaler stated it noticed the attacker manually logging into the account eight minutes after the credential theft, following it up by studying emails and checking the consumer’s profile data.
What’s extra, in some cases, the hacked e mail inboxes are subsequently used to ship extra phishing emails as a part of the identical marketing campaign to conduct enterprise e mail compromise (BEC) scams.
“Despite the fact that safety features similar to multi-factor authentication (MFA) add an additional layer of safety, they shouldn’t be thought-about as a silver bullet to guard in opposition to phishing assaults,” the researchers famous.
“With the usage of superior phishing kits (AiTM) and intelligent evasion methods, menace actors can bypass each conventional in addition to superior safety options.”