The decentralized file system answer often known as IPFS is changing into the brand new “hotbed” for internet hosting phishing websites, researchers have warned.
Cybersecurity agency Trustwave SpiderLabs, which disclosed specifics of the assault campaigns, stated it recognized at least 3,000 emails containing IPFS phishing URLs as an assault vector within the final three months.
IPFS, quick for InterPlanetary File System, is a peer-to-peer (P2P) community to retailer and share recordsdata and knowledge utilizing cryptographic hashes, as a substitute of URLs or filenames, as is noticed in a standard client-server strategy. Every hash varieties the idea for a novel content material identifier (CID).
The thought is to create a resilient distributed file system that enables knowledge to be saved throughout a number of computer systems. This is able to enable data to be accessed with out having to depend on third events corresponding to cloud storage suppliers, successfully making it proof against censorship.
“Taking down phishing content material saved on IPFS will be tough as a result of even whether it is eliminated in a single node, it might nonetheless be accessible on different nodes,” Trustwave researchers Karla Agregado and Katrina Udquin stated in a report.
Complicating issues additional is the shortage of a static Uniform Useful resource Identifier (URI) that can be utilized to find and block a single piece of malware-laden content material. This additionally means it may very well be a lot tougher to take down phishing websites hosted on IPFS.
The assaults noticed by Belief usually contain some sort of social engineering to decrease the guard of targets in an effort to coax them to click on fraudulent IPFS hyperlinks and activate the an infection chains.
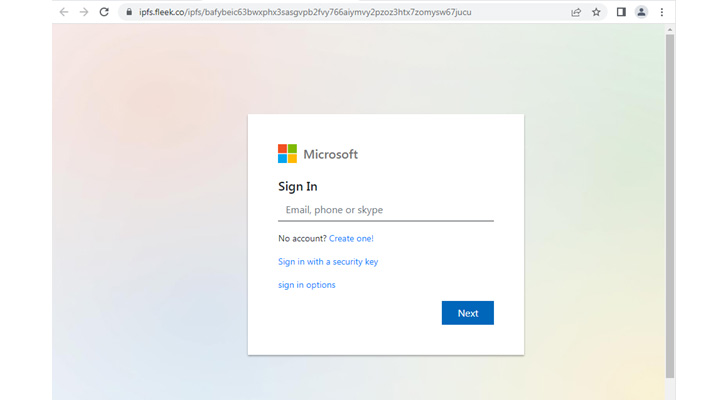
These domains immediate potential victims to enter their credentials to view a doc, monitor a bundle on DHL, or renew their Azure subscription, solely to siphon the e-mail addresses and passwords to a distant server.
“With knowledge persistence, strong community, and little regulation, IPFS is probably a really perfect platform for attackers to host and share malicious content material,” the researchers stated.
The findings come amid a bigger shift within the e mail menace panorama, with Microsoft’s plans to dam macros inflicting menace actors to adapt their techniques to distribute executables that may result in follow-on reconnaissance, knowledge theft, and ransomware.
Considered in that mild, the usage of IPFS marks one other evolution in phishing, giving attackers one other profitable playground to experiment with.
“Phishing methods have taken a leap by using the idea of decentralized cloud companies utilizing IPFS,” the researchers concluded.
“The spammers can simply camouflage their actions by internet hosting their content material in authentic hosting companies or use a number of URL redirection methods to assist thwart scanners utilizing URL repute or automated URL evaluation.”
What’s extra, these modifications have additionally been accompanied by way of off-the-shelf phishing kits – a pattern referred to as phishing-as-a-service (PhaaS) – that supply a fast and straightforward means for menace actors to mount assaults through e mail and SMS.
Certainly, a large-scale marketing campaign found final month was noticed utilizing a four-month-old PhaaS platform dubbed Robin Banks to plunder credentials and steal monetary data from clients of well-known banks in Australia, Canada, the U.Okay., and the U.S., cybersecurity agency IronNet disclosed this week.
“Whereas the first motivation for scammers utilizing this equipment seems to be monetary, the equipment does additionally ask victims for his or her Google and Microsoft credentials after they journey to the phishing touchdown web page, indicating it may be utilized by extra superior menace actors seeking to acquire preliminary entry to company networks for ransomware or different post-intrusion actions,” the researchers stated.