The U.S. Cybersecurity and Infrastructure Safety Company (CISA) on Thursday added two flaws to its Identified Exploited Vulnerabilities Catalog, citing proof of lively exploitation.
The 2 high-severity points relate to weaknesses in Zimbra Collaboration, each of which might be chained to realize unauthenticated distant code execution on affected e-mail servers –
- CVE-2022-27925 (CVSS rating: 7.2) – Distant code execution (RCE) by way of mboximport from authenticated person (fastened in variations 8.8.15 Patch 31 and 9.0.0 Patch 24 launched in March)
- CVE-2022-37042 – Authentication bypass in MailboxImportServlet (fastened in variations 8.8.15 Patch 33 and 9.0.0 Patch 26 launched in August)
“If you’re working a Zimbra model that’s older than Zimbra 8.8.15 patch 33 or Zimbra 9.0.0 patch 26 you must replace to the newest patch as quickly as doable,” Zimbra warned earlier this week.
CISA has not shared any info on the assaults exploiting the issues however cybersecurity agency Volexity described mass in-the-wild exploitation of Zimbra situations by an unknown menace actor.
In a nutshell, the assaults contain benefiting from the aforementioned authentication bypass flaw to achieve distant code execution on the underlying server by importing arbitrary information.
Volexity stated “it was doable to bypass authentication when accessing the identical endpoint (mboximport) utilized by CVE-2022-27925,” and that the flaw “might be exploited with out legitimate administrative credentials, thus making the vulnerability considerably extra crucial in severity.”
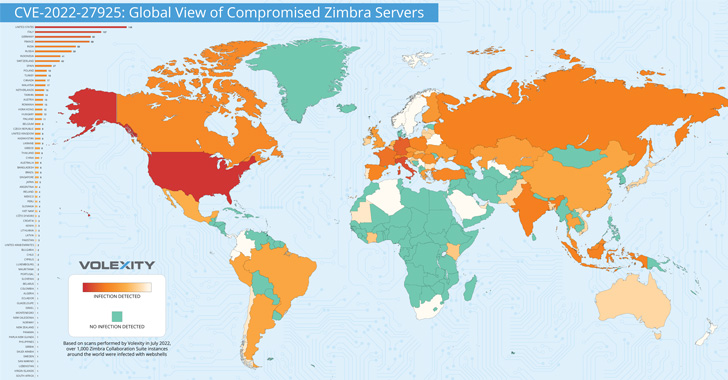
It additionally singled out over 1,000 situations globally that have been backdoored and compromised utilizing this assault vector, a few of which belong to authorities departments and ministries; navy branches; and corporations with billions of {dollars} of income.
The assaults, which transpired as lately as the top of June 2022, additionally concerned the deployment of internet shells to keep up long-term entry to the contaminated servers. High international locations with essentially the most compromised situations embody the U.S., Italy, Germany, France, India, Russia, Indonesia, Switzerland, Spain, and Poland.
“CVE-2022-27925 was initially listed as an RCE exploit requiring authentication,” Volexity stated. “When mixed with a separate bug, nonetheless, it turned an unauthenticated RCE exploit that made distant exploitation trivial.”
The disclosure comes per week after CISA added one other Zimbra-related bug, CVE-2022-27924, to the catalog, which, if exploited, may permit attackers to steal cleartext credentials from customers of the focused situations.