A brand new focused phishing marketing campaign has zoomed in on a two-factor authentication answer referred to as Kavach that is utilized by Indian authorities officers.
Cybersecurity agency Securonix dubbed the exercise STEPPY#KAVACH, attributing it to a menace actor often called SideCopy primarily based on tactical overlaps with prior assaults.
“.LNK recordsdata are used to provoke code execution which finally downloads and runs a malicious C# payload, which features as a distant entry trojan (RAT),” Securonix researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov mentioned in a brand new report.
SideCopy, a hacking crew believed to be of Pakistani origin and lively since a minimum of 2019, is claimed to share ties with one other actor referred to as Clear Tribe (aka APT36 or Mythic Leopard).
It is also identified to impersonate assault chains leveraged by SideWinder, a prolific nation-state group that disproportionately singles out Pakistan-based navy entities, to deploy its personal toolset.
That mentioned, this isn’t the primary time Kavach has emerged as a goal for the actor. In July 2021, Cisco Talos detailed an espionage operation that was undertaken to steal credentials from Indian authorities staff.
Kavach-themed decoy apps have since been co-opted by Clear Tribe in its assaults focusing on India because the begin of the 12 months.
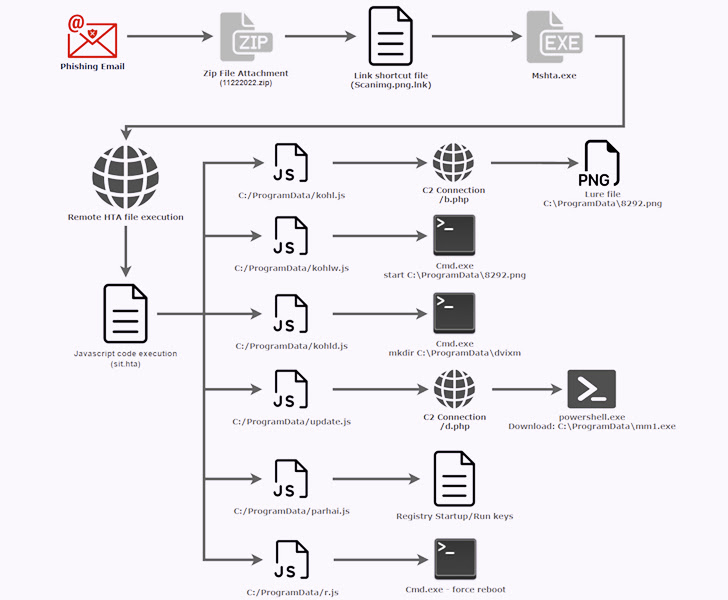
The newest assault sequence noticed by Securonix over the previous couple of weeks entails utilizing phishing emails to lure potential victims into opening a shortcut file (.LNK) to execute a distant .HTA payload utilizing the mshta.exe Home windows utility.
The HTML software, the corporate mentioned, “was found being hosted on a possible compromised web site, nested inside an obscure ‘gallery’ listing designed to retailer among the web site’s photographs.”
The compromised web site in query is incometaxdelhi[.]org, the official web site for India’s Earnings Tax division pertaining to the Delhi area. The malicious file is now not out there on the portal.
Within the subsequent section, working the .HTA file results in the execution of obfuscated JavaScript code that is designed to indicate a decoy picture file that options an announcement from the Indian Ministry of Defence a 12 months in the past in December 2021.
The JavaScript code additional downloads an executable from a distant server, establishes persistence by way of Home windows Registry modifications, and reboots the machine to mechanically launch the binary put up startup.
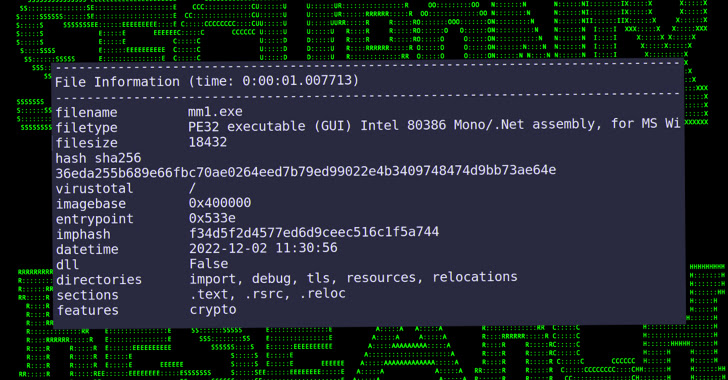
The binary file, for its half, features as a backdoor that permits the menace actor to execute instructions despatched from an attacker-controlled area, fetch and run extra payloads, take screenshots, and exfiltrate recordsdata.
The exfiltration part additionally consists of an choice to particularly seek for a database file (“kavach.db”) created by the Kavach app on the system to retailer the credentials.
It is value noting that the aforementioned an infection chain was disclosed by the MalwareHunterTeam in a collection of tweets on December 8, 2022, describing the distant entry trojan as MargulasRAT.
“Primarily based on correlated information from the binary samples obtained of the RAT utilized by the menace actors, this marketing campaign has been happening in opposition to Indian targets undetected for the final 12 months,” the researchers mentioned.