The risk actors behind a large-scale adversary-in-the-middle (AiTM) phishing marketing campaign concentrating on enterprise customers of Microsoft e-mail companies have additionally set their sights on Google Workspace customers.
“This marketing campaign particularly focused chief executives and different senior members of varied organizations which use [Google Workspace],” Zscaler researchers Sudeep Singh and Jagadeeswar Ramanukolanu detailed in a report revealed this month.
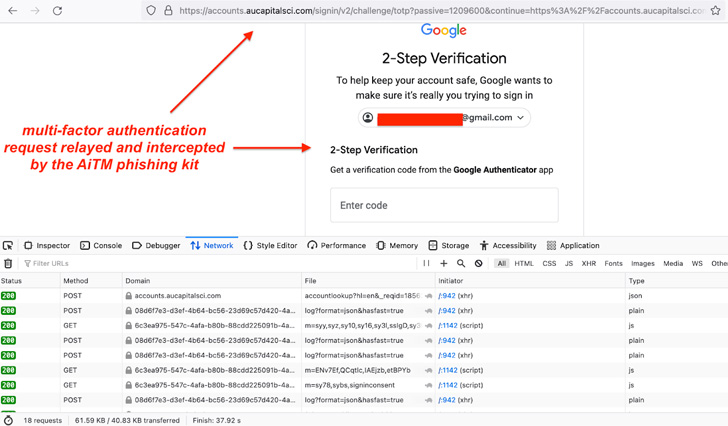
The AitM phishing assaults are mentioned to have commenced in mid-July 2022, following an analogous modus operandi as that of a social engineering marketing campaign designed to siphon customers’ Microsoft credentials and even bypass multi-factor authentication.
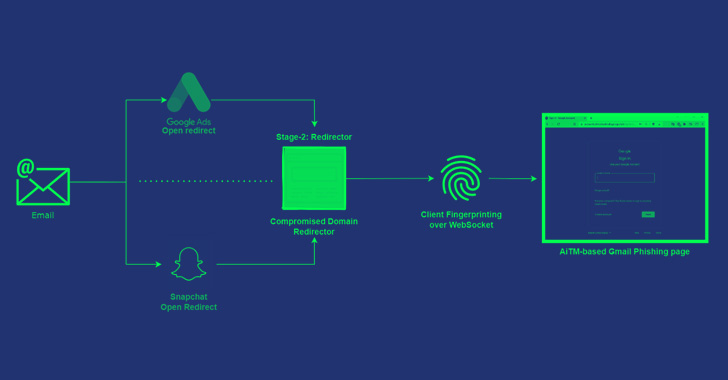
The low-volume Gmail AiTM phishing marketing campaign additionally entails utilizing the compromised emails of chief executives to conduct additional phishing assaults by the risk actor, with the assaults additionally using a number of compromised domains as an intermediate URL redirector to take the victims to the touchdown web page.
Assault chains contain sending password expiry emails to potential targets that comprise an embedded malicious hyperlink to supposedly “lengthen your entry,” tapping which takes the recipient to open redirect pages of Google Advertisements and Snapchat to load the phishing web page URL.
Beside open redirect abuse, a second variant of the assaults depends on contaminated websites which host a Base64-encoded model of the next-stage redirector and the sufferer’s e-mail deal with within the URL. This intermediate redirector is a JavaScript code that factors to a Gmail phishing web page.
In a single occasion highlighted by Zscaler, the redirector web page used within the Microsoft AiTM phishing assault on July 11, 2022, was up to date to take the consumer to a Gmail AiTM phishing web page, connecting the 2 campaigns to the identical risk actor.
“There was additionally an overlap of infrastructure, and we even recognized a number of instances through which the risk actor switched from Microsoft AiTM phishing to Gmail phishing utilizing the identical infrastructure,” the researchers mentioned.
The findings are a sign that multi-factor authentication safeguards alone can not provide protections towards superior phishing assaults, necessitating that customers scrutinize URLs earlier than getting into credentials and chorus from opening attachments or clicking on hyperlinks in emails despatched from untrusted or unknown sources.