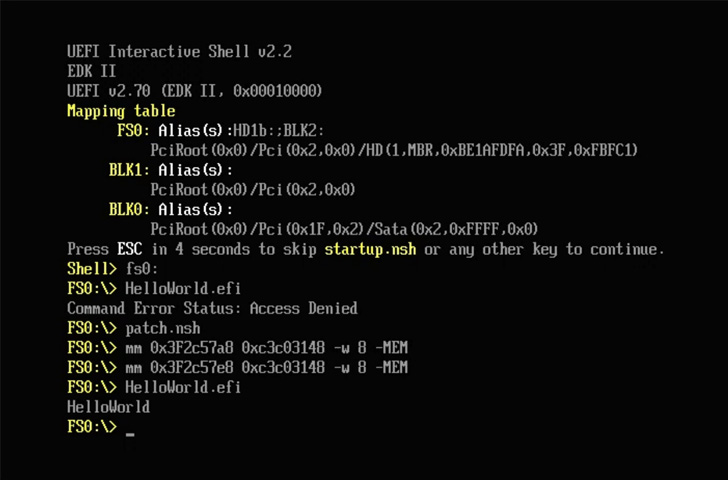
A safety function bypass vulnerability has been uncovered in three signed third-party Unified Extensible Firmware Interface (UEFI) boot loaders that enable bypass of the UEFI Safe Boot function.
“These vulnerabilities will be exploited by mounting the EFI System Partition and changing the present bootloader with the weak one, or modifying a UEFI variable to load the weak loader as a substitute of the present one,” {hardware} safety agency Eclypsium stated in a report shared with The Hacker Information.
The next vendor-specific boot loaders, which had been signed and authenticated by Microsoft, have been discovered weak to the bypass and have been patched as a part of the tech big’s Patch Tuesday replace launched this week –
Safe Boot is a safety normal designed to thwart malicious packages from loading when a pc begins up (boots) and guarantee solely the software program that’s trusted by the Unique Gear Producer (OEM) is launched.
In different phrases, profitable exploitation of the issues might allow an adversary to bypass safety guardrails at startup and execute arbitrary unsigned code in the course of the boot course of.
This will have additional knock-on results, enabling a nasty actor to achieve entrenched entry and set up persistence on a bunch via in a fashion that may survive working system reinstalls and onerous drive replacements, to not point out utterly bypassing detection by safety software program.
Calling CVE-2022-34302 “much more stealthy,” Eclypsium famous the New Horizon Datasys vulnerability will not be solely trivial to use within the wild, however also can “allow much more advanced evasions reminiscent of disabling safety handlers.”
Safety handlers, for example, can embrace Trusted Platform Module (TPM) measurements and signature checks, Eclypsium researchers Mickey Shkatov and Jesse Michael stated.
It is price noting that exploiting these vulnerabilities requires an attacker to have administrator privileges, though gaining native privilege escalation will not be insurmountable.
“Very similar to BootHole, these vulnerabilities spotlight the challenges of making certain the boot integrity of units that depend on a posh provide chain of distributors and code working collectively,” the researchers concluded, including “these points spotlight how easy vulnerabilities in third-party code can undermine the whole course of.”