Cybersecurity researchers have uncovered new variants of the ChromeLoader information-stealing malware, highlighting its evolving characteristic set in a brief span of time.
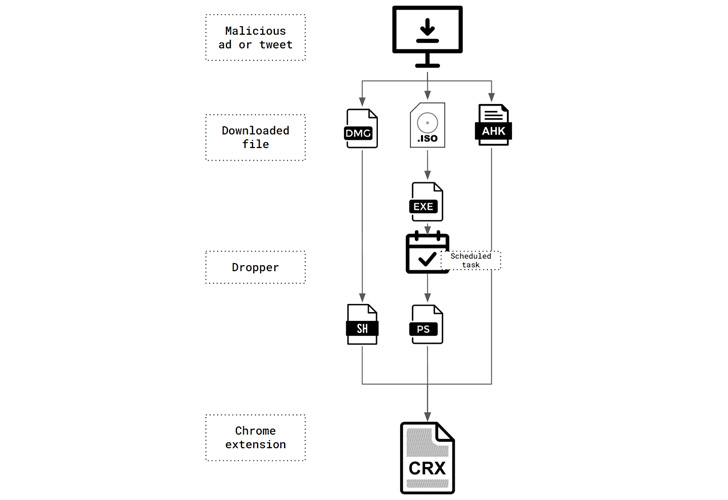
Primarily used for hijacking victims’ browser searches and presenting ads, ChromeLoader got here to mild in January 2022 and has been distributed within the type of ISO or DMG file downloads marketed by way of QR codes on Twitter and free gaming websites.
ChromeLoader has additionally been codenamed Choziosi Loader and ChromeBack by the broader cybersecurity group. What makes the adware notable is that it is original as a browser extension versus a Home windows executable (.exe) or Dynamic Hyperlink Library (.dll).
The infections usually work by engaging unsuspecting customers into downloading film torrents or cracked video video games by way of malvertising campaigns on pay-per-install websites and social media.
Moreover requesting invasive permissions to entry browser information and manipulate internet requests, it is also designed to seize customers’ search engine queries on Google, Yahoo, and Bing, successfully permitting the risk actors to reap their on-line habits.
Whereas the primary Home windows variant of ChromeLoader malware was noticed in January, a macOS model of the malware emerged in March to distribute the rogue Chrome extension (model 6.0) by way of sketchy disk picture (DMG) recordsdata.
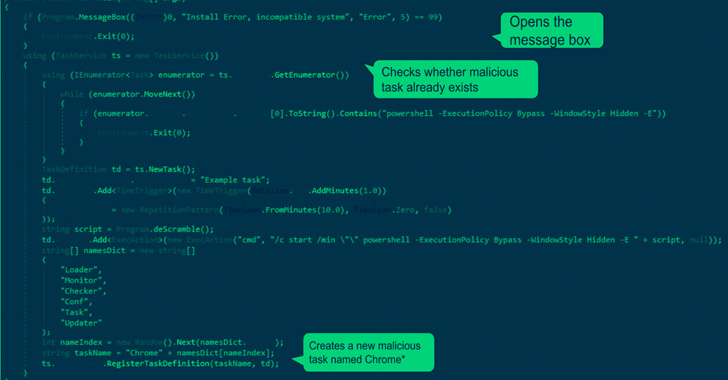
However a brand new evaluation from Palo Alto Networks Unit 42 signifies that the earliest recognized assault involving the malware occurred in December 2021 utilizing an AutoHotKey-compiled executable instead of the later-observed ISO recordsdata.
“This malware was an executable file written utilizing AutoHotKey (AHK) — a framework used for scripting automation,” Unit 42 researcher Nadav Barak mentioned, including it was used to drop “model 1.0” of the browser add-on.
This primary model can also be mentioned to lack obfuscation capabilities, a characteristic that has been picked up in subsequent iterations of the malware to hide its objective and malicious code.
Additionally noticed since March 2022 is a beforehand undocumented marketing campaign utilizing the 6.0 model of the Chrome extension and depends on an ISO picture that comprises a seemingly benign Home windows shortcut, however, in actuality, acts as a conduit to launch a hidden file within the mounted picture which deploys the malware.
“This malware demonstrates how decided cybercriminals and malware authors may be: In a short while interval, the authors of ChromeLoader launched a number of completely different code variations, used a number of programming frameworks, enhanced options, superior obfuscators, fastened points, and even including cross-OS help focusing on each Home windows and macOS,” Barak mentioned.