The operators behind the Qakbot malware are reworking their supply vectors in an try to sidestep detection.
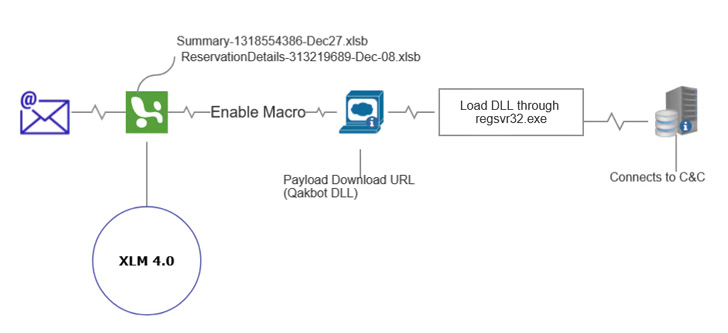
“Most just lately, menace actors have remodeled their methods to evade detection through the use of ZIP file extensions, engaging file names with widespread codecs, and Excel (XLM) 4.0 to trick victims into downloading malicious attachments that set up Qakbot,” Zscaler Threatlabz researchers Tarun Dewan and Aditya Sharma mentioned.
Different strategies adopted by the group embody code obfuscation, introducing new layers within the assault chain from preliminary compromise to execution, and utilizing a number of URLs in addition to unknown file extensions (e.g., .OCX, .ooccxx, .dat, or .gyp) to ship the payload.
Additionally referred to as QBot, QuackBot, or Pinkslipbot, Qakbot has been a recurring menace since late 2007, evolving from its preliminary days as a banking trojan to a modular info stealer able to deploying next-stage payloads akin to ransomware.
“Qakbot is a versatile post-exploitation instrument that comes with numerous layers of protection evasion methods designed to reduce detections,” Fortinet disclosed in December 2021.
“Qakbot’s modular design and notorious resiliency within the face of conventional signature-based detection make it a fascinating first alternative for a lot of financially motivated teams (cyber criminals).”
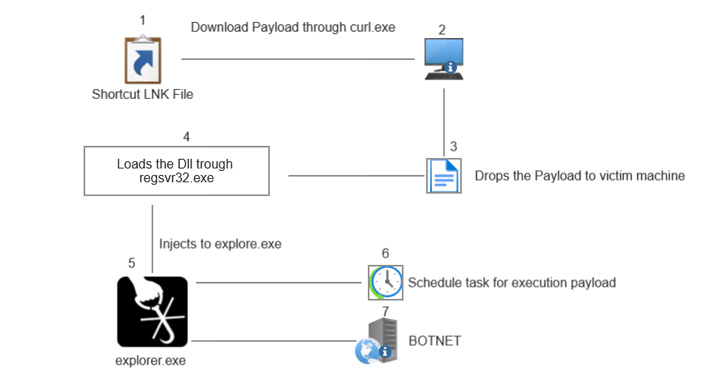
The shifting ways adopted by the malware from XLM macros in early 2022 to .LNK information in Could is seen as an try to counter Microsoft’s plans to dam Workplace macros by default in April 2022, a call it has since quickly rolled again.
As well as, additional modifications embody using PowerShell to obtain the DLL malware and a change from regsvr32.exe to rundlll32.exe to load the payload, in what the researchers described as a “clear signal of Qakbot evolving to evade up to date safety practices and defenses.”