A widespread software program provide chain assault has focused the NPM bundle supervisor a minimum of since December 2021 with rogue modules designed to steal information entered in kinds by customers on web sites that embody them.
The coordinated assault, dubbed IconBurst by ReversingLabs, includes no fewer than two dozen NPM packages that embody obfuscated JavaScript, which comes with malicious code to reap delicate information from kinds embedded downstream cell functions and web sites.
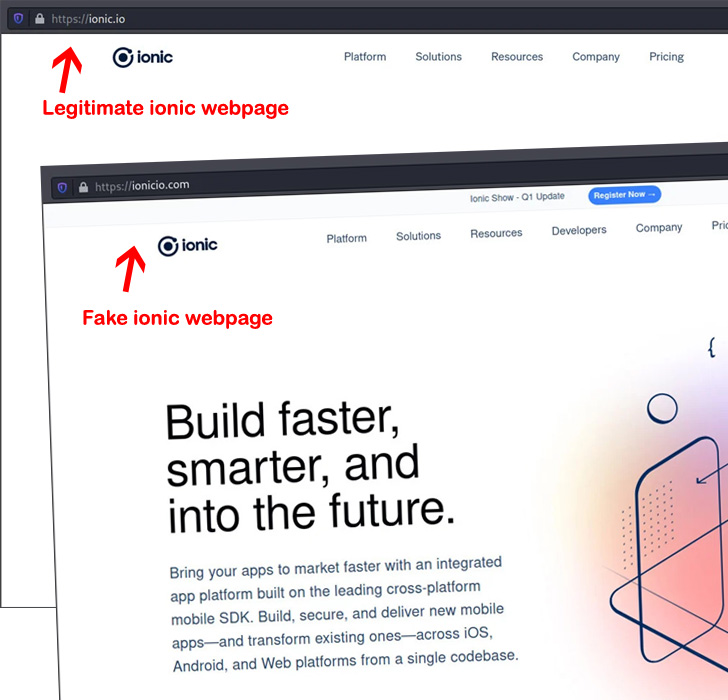
“These clearly malicious assaults relied on typo-squatting, a method wherein attackers provide up packages by way of public repositories with names which might be just like — or widespread misspellings of — professional packages,” safety researcher Karlo Zanki mentioned in a Tuesday report. “Attackers impersonated high-traffic NPM modules like umbrellajs and packages printed by ionic.io.”
The packages in query, most of which have been printed within the final months, have been collectively downloaded greater than 27,000 occasions thus far. Worse, a majority of the modules proceed to be obtainable for obtain from the repository.
Among the most obtain malicious modules are listed under –
- icon-package (17,774)
- ionicio (3,724)
- ajax-libs (2,440)
- footericon (1,903)
- umbrellaks (686)
- ajax-library (530)
- pack-icons (468)
- icons-package (380)
- swiper-bundle (185), and
- icons-packages (170)
In a single occasion noticed by ReversingLabs, information exfiltrated by icon-package was routed to a site named ionicio[.]com, a lookalike web page engineered to resemble the professional ionic[.]io web site.
The malware authors behind the marketing campaign additional switched up their techniques in latest months to assemble info from each type component on the net web page, indicating an aggressive method to information harvesting.
“The decentralized and modular nature of utility growth signifies that functions and providers are solely as sturdy as their least safe part,” Zanki famous. “The success of this assault […] underscores the freewheeling nature of utility growth, and the low boundaries to malicious and even weak code coming into delicate functions and IT environments.”