The North Korean nation-state group Kimusky has been linked to a brand new set of malicious actions directed in opposition to political and diplomatic entities positioned in its southern counterpart in early 2022.
Russian cybersecurity agency Kaspersky codenamed the cluster GoldDragon, with the an infection chains resulting in the deployment of Home windows malware designed to file lists, person keystrokes, and saved internet browser login credentials.
Included among the many potential victims are South Korean college professors, suppose tank researchers, and authorities officers.
Kimsuky, also called Black Banshee, Thallium, and Velvet Chollima, is the identify given to a prolific North Korean superior persistent risk (APT) group that targets entities globally, however with a major give attention to South Korea, to achieve intelligence on varied matters of curiosity to the regime.
Recognized to be working since 2012, the group has a historical past of using social engineering techniques, spear-phishing, and watering gap assaults to exfiltrate desired info from victims.
Late final month, cybersecurity agency Volexity attributed the actor to an intelligence gathering mission designed to siphon electronic mail content material from Gmail and AOL through a malicious Chrome browser extension dubbed Sharpext.
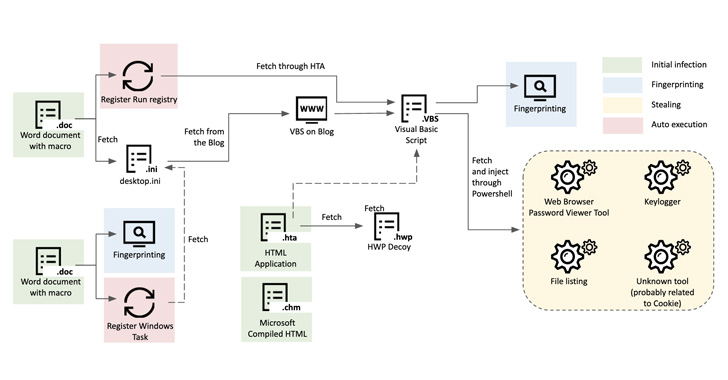
The newest marketing campaign follows an identical modus operandi whereby the assault sequence is initiated through spear-phishing messages containing macro-embedded Microsoft Phrase paperwork that purportedly function content material associated to geopolitical points within the area.
Different preliminary entry routes are additionally stated to make the most of HTML Software (HTA) and Compiled HTML Assist (CHM) recordsdata as decoys to compromise the system.
Whatever the methodology used, the preliminary entry is adopted by dropping a Visible Fundamental Script from a distant server that is orchestrated to fingerprint the machine and retrieve extra payloads, together with an executable able to exfiltrating delicate info.
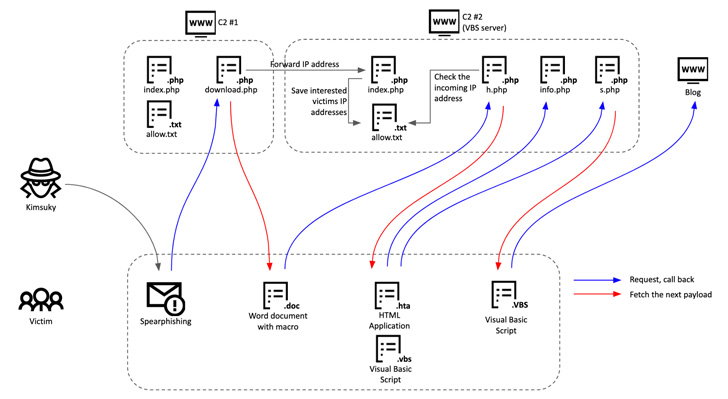
What’s novel in regards to the assault is the transmission of the sufferer’s electronic mail tackle to the command-and-control (C2) server ought to the recipient click on a hyperlink within the electronic mail to obtain extra paperwork. If the request does not include an anticipated electronic mail tackle, a benign doc is returned.
To additional complicate the kill chain, the first-stage C2 server forwards the sufferer’s IP tackle to a different VBS server, which then compares it with an incoming request that is generated after the goal opens the lure doc.
The “sufferer verification methodology” within the two C2 servers ensures that the VBScript is delivered solely when the IP tackle checks are profitable, indicating a extremely focused method.
“The Kimsuky group repeatedly evolves its malware an infection schemes and adopts novel methods to hinder evaluation,” Kaspersky researcher Seongsu Park stated. “The primary issue in monitoring this group is that it is powerful to amass a full-infection chain.”