Researchers have make clear a brand new hybrid malware marketing campaign focusing on each Android and Home windows working methods in a bid to broaden its pool of victims.
The assaults entail the usage of totally different malware reminiscent of ERMAC, Erbium, Aurora, and Laplas, in accordance with a ThreatFabric report shared with The Hacker Information.
“This marketing campaign resulted in 1000’s of victims,” the Dutch cybersecurity firm stated, including, “Erbium stealer efficiently exfiltrated knowledge from extra then 1,300 victims.”
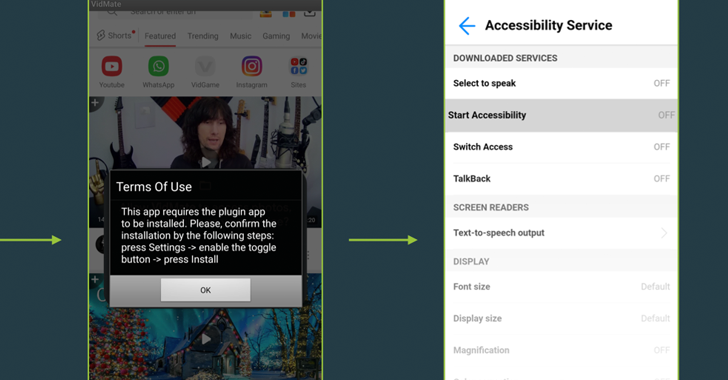
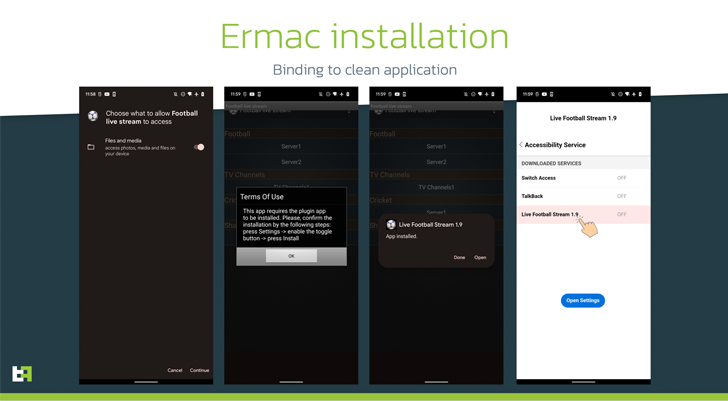
The ERMAC infections start with a fraudulent web site that claims to supply Wi-Fi authorization software program for Android and Home windows that, when put in, comes with options to steal seed phrases from crypto wallets and different delicate knowledge.
ThreatFabric stated it additionally discovered numerous malicious apps that have been trojanized variations of professional apps like Instagram, with the operators utilizing them as droppers to ship the obfuscated malicious payload.
The rogue apps, dubbed Zombinder, are stated to have been developed utilizing an APK binding service marketed on the darkish internet by a widely known risk actor since March 2022.
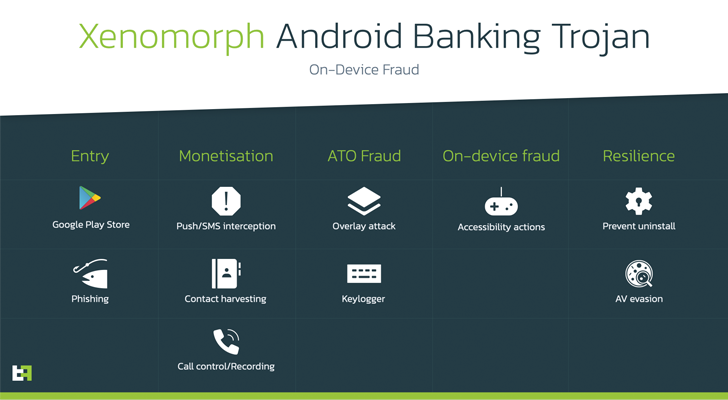
Such zombie apps have been used to distribute Android banking trojans like SOVA and Xenomorph focusing on clients in Spain, Portugal, and Canada, amongst others.
Curiously, the obtain choice for Home windows on the booby-trapped web site distributing ERMAC is designed to deploy the Erbium and Aurora info stealers on the compromised system.
Erbium, which is a malware-as-a-service (MaaS) licensed for $1,000 per 12 months, not solely steals passwords and bank card info, however has additionally been noticed appearing as a conduit to drop the Laplas clipper that is used to hijack crypto transactions.
“The presence of such all kinds of trojans may also point out that the malicious touchdown web page is utilized by a number of actors and offered to them as part of a third-party distribution service,” the researchers theorized.