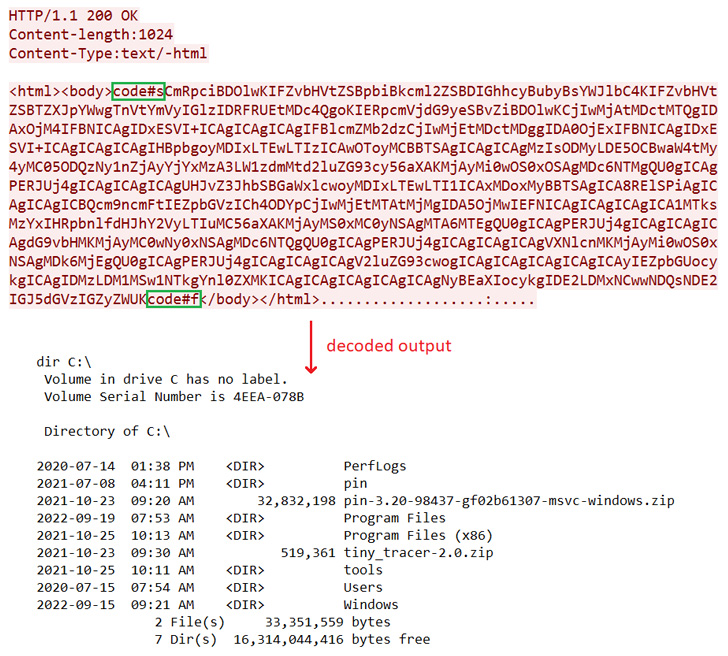
A menace actor tracked as Polonium has been linked to over a dozen extremely focused assaults geared toward Israelian entities with seven totally different customized backdoors since a minimum of September 2021.
The intrusions had been geared toward organizations in varied verticals, akin to engineering, info expertise, legislation, communications, branding and advertising and marketing, media, insurance coverage, and social companies, cybersecurity agency ESET stated.
Polonium is the chemical element-themed moniker given by Microsoft to a classy operational group that is believed to be based mostly in Lebanon and is thought to completely strike Israeli targets.
Actions undertaken by the group first got here to mild earlier this June when the Home windows maker disclosed it suspended greater than 20 malicious OneDrive accounts created by the adversary for command-and-control (C2) functions.
Core to the assaults has been the usage of implants coined CreepyDrive and CreepyBox for his or her means to exfiltrate delicate knowledge to actor-controlled OneDrive and Dropbox accounts. Additionally deployed is a PowerShell backdoor dubbed CreepySnail.
ESET’s newest discovery of 5 extra beforehand undocumented backdoors brings into focus an lively espionage-oriented menace actor that is consistently refining and retooling its malware arsenal.
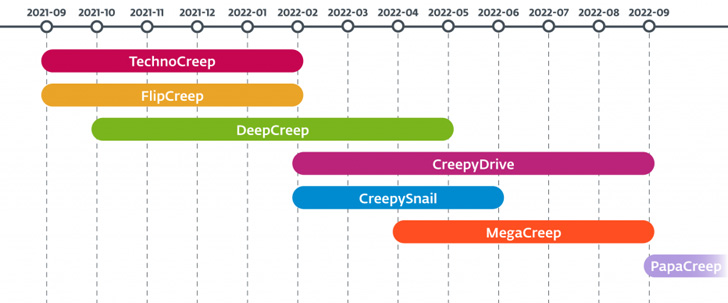
“The quite a few variations and adjustments Polonium launched into its customized instruments present a steady and long-term effort to spy on the group’s targets,” ESET researcher Matías Porolli stated. “The group does not appear to have interaction in any sabotage or ransomware actions.”
The record of bespoke hacking instruments is as follows –
- CreepyDrive/CreepyBox – A PowerShell backdoor that reads and executes instructions from a textual content file saved on OneDrive or Dropbox.
- CreepySnail – A PowerShell backdoor that receives instructions from the attacker’s personal C2 server
- DeepCreep – A C# backdoor that reads instructions from a textual content file saved in Dropbox accounts and exfiltrates knowledge
- MegaCreep – A C# backdoor that reads instructions from a textual content file saved in Mega cloud storage service
- FlipCreep – A C# backdoor that reads instructions from a textual content file saved in an FTP server and exfiltrates knowledge
- TechnoCreep – A C# backdoor that communicates with the C2 server by way of TCP sockets to execute instructions and exfiltrate knowledge
- PapaCreep – A C++ backdoor that may obtain and execute instructions from a distant server by way of TCP sockets
PapaCreep, noticed as just lately as September 2022, is a modular malware that comprises 4 totally different elements which might be designed to run instructions, obtain and ship instructions and their outputs, and add and obtain recordsdata.
The Slovak cybersecurity agency stated it additionally uncovered a number of different modules answerable for logging keystrokes, capturing screenshots, taking photographs by way of webcam, and establishing a reverse shell on the compromised machine.
Regardless of the abundance of malware utilized within the assaults, the preliminary entry vector used to breach the networks is at present unknown, though it is suspected that it could have concerned the exploitation of VPN flaws.
“A lot of the group’s malicious modules are small, with restricted performance,” Porolli stated. “They wish to divide the code of their backdoors, distributing malicious performance into varied small DLLs, maybe anticipating that defenders or researchers won’t observe the entire assault chain.”