As ransomware infections have developed from purely encrypting knowledge to schemes similar to double and triple extortion, a brand new assault vector is more likely to set the stage for future campaigns.
Known as Ransomware for IoT or R4IoT by Forescout, it is a “novel, proof-of-concept ransomware that exploits an IoT system to realize entry and transfer laterally in an IT [information technology] community and impression the OT [operational technology] community.”
This potential pivot relies on the fast progress within the variety of IoT units in addition to the convergence of IT and OT networks in organizations.
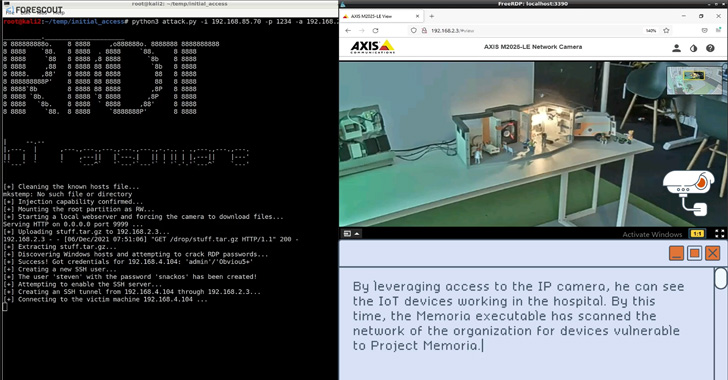
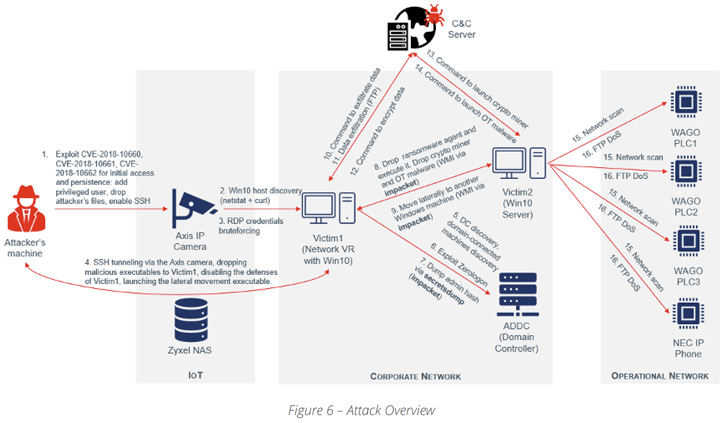
The last word purpose of R4IoT is to leverage uncovered and weak IoT units similar to IP cameras to realize an preliminary foothold, adopted by deploying ransomware within the IT community and making the most of poor operational safety practices to carry mission-critical processes hostage.
“By compromising IoT, IT, and OT property, R4IoT goes past the same old encryption and knowledge exfiltration to trigger bodily disruption of enterprise operations,” the researchers stated, thereby including a further layer of extortion to a conventional ransomware assault.
Put otherwise, R4IoT is a brand new type of malware that brings collectively an IoT entry level and ransomware-related lateral motion and encryption on an IT community, inflicting an prolonged impression on each IT and OT networks.
In a hypothetical situation, this might entail compromising a machine within the company community to not solely drop ransomware but additionally retrieve further payloads from a distant server to deploy cryptocurrency miners and launch denial-of-service (DoS) assaults towards OT property.
To mitigate each the probability and the impression of potential R4IoT incidents, organizations are really helpful to establish and patch weak units, implement community segmentation, implement robust password insurance policies, and monitor HTTPS connections, FTP periods, and community site visitors.
“Ransomware has been essentially the most prevalent menace of the previous few years, and thus far, it has largely leveraged vulnerabilities in conventional IT gear to cripple organizations,” the researchers concluded.
“However new connectivity developments have added a quantity and a variety of OT and IoT units which have elevated danger in almost each enterprise.”