Excessive-severity safety vulnerabilities have been disclosed in several endpoint detection and response (EDR) and antivirus (AV) merchandise that may very well be exploited to show them into knowledge wipers.
“This wiper runs with the permissions of an unprivileged person but has the power to wipe nearly any file on a system, together with system recordsdata, and make a pc fully unbootable,” SafeBreach Labs researcher Or Yair mentioned. “It does all that with out implementing code that touches the goal recordsdata, making it absolutely undetectable.”
EDR software program, by design, are able to regularly scanning a machine for probably suspicious and malicious recordsdata, and taking applicable motion, akin to deleting or quarantining them.
The thought, in a nutshell, is to trick weak safety merchandise into deleting professional recordsdata and directories on the system and render the machine inoperable by making use of specifically crafted paths.
That is achieved by making the most of what’s known as a junction level (aka tender hyperlink), the place a listing serves as an alias to a different listing on the pc.
Put in a different way, between the window the EDR software program identifies a file as malicious and makes an attempt to delete the file from the system, the attacker makes use of a junction to level the software program in the direction of a unique path, like C: drive.
The strategy, nonetheless, did not lead to a wipe as EDRs prevented additional entry to a file after it was flagged as malicious. What’s extra, ought to the rogue file be deleted by the person, the software program was intelligent sufficient to detect the deletion and cease itself from appearing on it.
The last word resolution arrived within the type of a wiper device, dubbed Aikido, that triggers the privileged delete by making a malicious file at a decoy listing and never granting it any permission, inflicting the EDRs to postpone the delete till subsequent reboot.
Given this new assault interval, all an adversary has to do is delete the listing containing the rogue file, create a junction to level to the goal listing to be deleted, and reboot the system.
Profitable weaponization of the approach may outcome within the deletion of system recordsdata like drivers, stopping the working system from booting. It may also be abused to take away all recordsdata from administrator person directories.
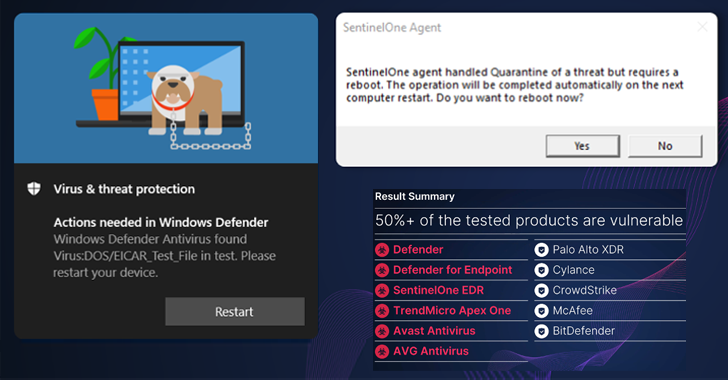
Out of 11 safety merchandise that had been examined, six had been discovered weak to the zero-day wiper exploit, prompting the distributors to launch updates to handle the shortcoming –
“The wiper executes its malicious actions utilizing essentially the most trusted entity on the system — the EDR or AV,” Yair mentioned. “EDRs and AVs don’t forestall themselves from deleting recordsdata.”