Particulars have emerged a few now-patched safety flaw in Home windows Widespread Log File System (CLFS) that could possibly be exploited by an attacker to realize elevated permissions on compromised machines.
Tracked as CVE-2022-37969 (CVSS rating: 7.8), the difficulty was addressed by Microsoft as a part of its Patch Tuesday updates for September 2022, whereas additionally noting that it was being actively exploited within the wild.
“An attacker should have already got entry and the power to run code on the goal system,” the corporate famous in its advisory. “This method doesn’t enable for distant code execution in instances the place the attacker doesn’t have already got that potential on the goal system.”
It additionally credited researchers from CrowdStrike, DBAPPSecurity, Mandiant, and Zscaler for reporting the vulnerability with out delving into further specifics surrounding the character of the assaults.
Now, the Zscaler ThreatLabz researcher crew has disclosed that it captured an in-the-wild exploit for the then zero-day on September 2, 2022.
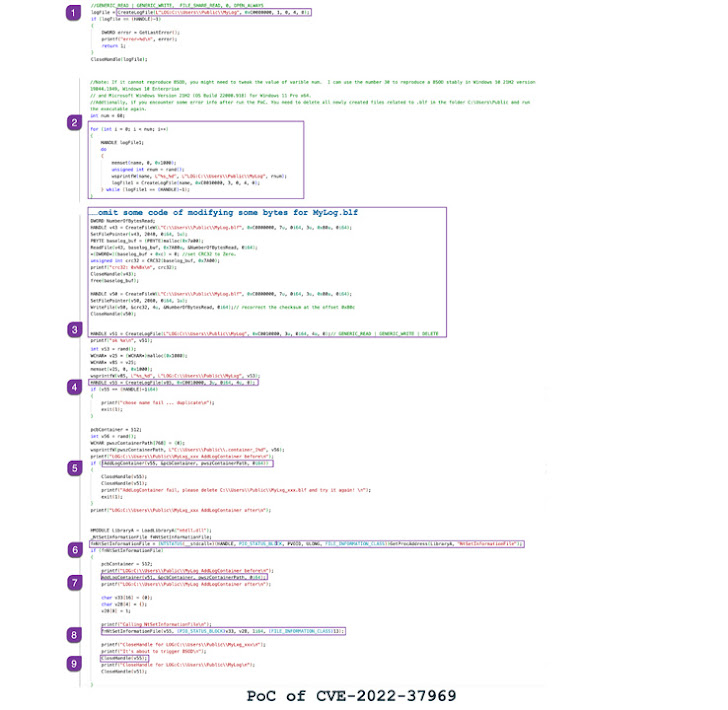
“The reason for the vulnerability is because of the lack of a strict bounds examine on the sector cbSymbolZone within the Base File Header for the bottom log file (BLF) in CLFS.sys,” the cybersecurity agency mentioned in a root trigger evaluation shared with The Hacker Information.
“If the sector cbSymbolZone is ready to an invalid offset, an out-of-bounds write will happen on the invalid offset.”
CLFS is a general-purpose logging service that can be utilized by software program functions operating in each user-mode or kernel-mode to document knowledge in addition to occasions and optimize log entry.
Among the use instances related to CLFS embody on-line transaction processing (OLTP), community occasions logging, compliance audits, and risk evaluation.
In response to Zscaler, the vulnerability is rooted in a metadata block referred to as base document that is current in a base log file, which is generated when a log file is created utilizing the CreateLogFile() perform.
“[Base record] incorporates the image tables that retailer data on the assorted consumer, container and safety contexts related to the Base Log File, in addition to accounting data on these,” in response to Alex Ionescu, chief architect at Crowdstrike.
Because of this, a profitable exploitation of CVE-2022-37969 by way of a specifically crafted base log file may result in reminiscence corruption, and by extension, induce a system crash (aka blue display of demise or BSoD) in a dependable method.
That mentioned, a system crash is simply one of many outcomes that arises out of leveraging the vulnerability, for it may be weaponized to realize privilege escalation.
Zscaler has additional made out there proof-of-concept (PoC) directions to set off the safety gap, making it important that customers of Home windows improve to the newest model to mitigate potential threats.