Cybersecurity researchers have disclosed particulars of now-patched flaws in Zendesk Discover that would have been exploited by an attacker to realize unauthorized entry to info from buyer accounts which have the function turned on.
“Earlier than it was patched, the flaw would have allowed risk actors to entry conversations, e-mail addresses, tickets, feedback, and different info from Zendesk accounts with Discover enabled,” Varonis stated in a report shared with The Hacker Information.
The cybersecurity agency stated there was no proof to recommend that the problems have been actively exploited in real-world assaults. No motion is required on the a part of the shoppers.
Zendesk Discover is a reporting and analytics answer that enables organizations to “view and analyze key details about your prospects, and your assist sources.”
In accordance with the safety software program firm, exploitation of the shortcoming first requires an attacker to register for the ticketing service of its sufferer’s Zendesk account as a brand new exterior person, a function that is seemingly enabled by default to permit end-users to submit assist tickets.
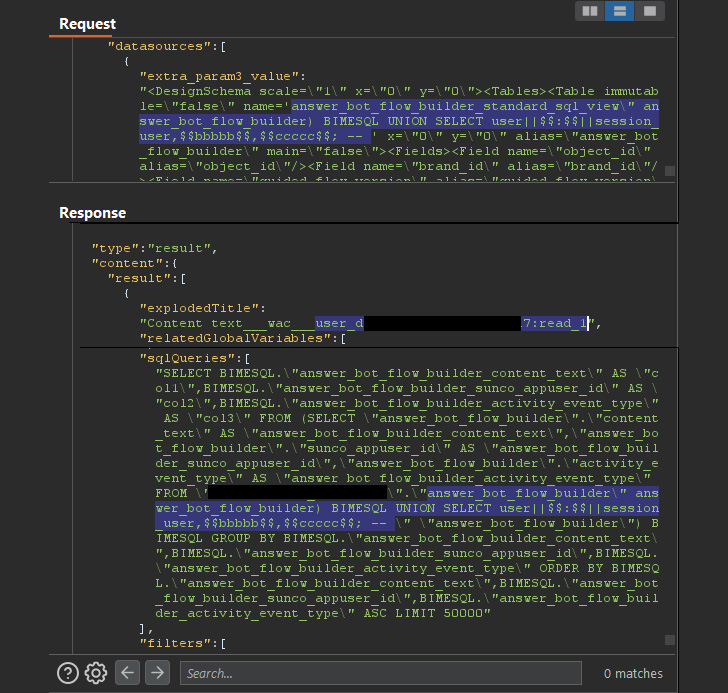
The vulnerability pertains to an SQL injection in its GraphQL API that might be abused to exfiltrate all info saved within the database as an admin person, together with e-mail addresses, tickets, and conversations with stay brokers.
A second flaw considerations a logic entry subject related to a question execution API, which was configured to run the queries with out checking if the “person” making the decision had enough permission to take action.
“This meant {that a} newly created end-user might invoke this API, change the question, and steal information from any desk within the goal Zendesk account’s RDS, no SQLi required,”
Varonis stated the problems have been disclosed to Zendesk on August 30, following which the weaknesses have been rectified by the corporate on September 8, 2022.