A well-liked npm package deal with greater than 3.5 million weekly downloads has been discovered weak to an account takeover assault.
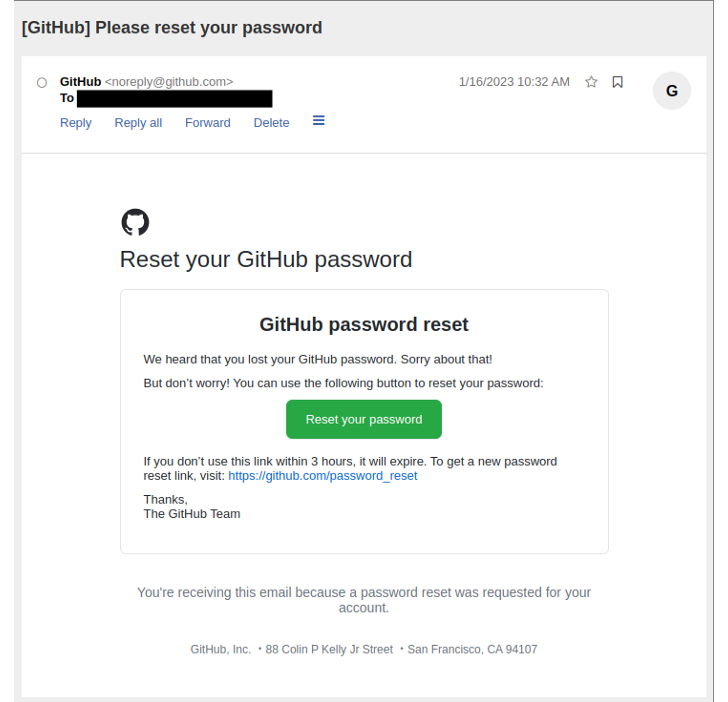
“The package deal might be taken over by recovering an expired area identify for certainly one of its maintainers and resetting the password,” software program provide chain safety firm Illustria mentioned in a report.
Whereas npm’s safety protections restrict customers to have just one energetic electronic mail deal with per account, the Israeli agency mentioned it was in a position to reset the GitHub password utilizing the recovered area.
The assault, in a nutshell, grants a menace actor entry to the package deal’s related GitHub account, successfully making it attainable to publish trojanized variations to the npm registry that may be weaponized to conduct provide chain assaults at scale.
That is achieved by profiting from a GitHub Motion that is configured within the repository to robotically publish the packages when new code modifications are pushed.
“Regardless that the maintainer’s npm person account is correctly configured with [two-factor authentication], this automation token bypasses it,” Bogdan Kortnov, co-founder and CTO of Illustria, mentioned.
Illustria didn’t disclose the identify of the module, however famous that it reached out to its maintainer, who has since taken steps to safe the account.
This isn’t the primary time developer accounts have been discovered weak to takeovers in recent times. In Could 2022, a menace actor registered an expired area utilized by the maintainer related to the ctx Python package deal to grab management of the account and distributed a malicious model.