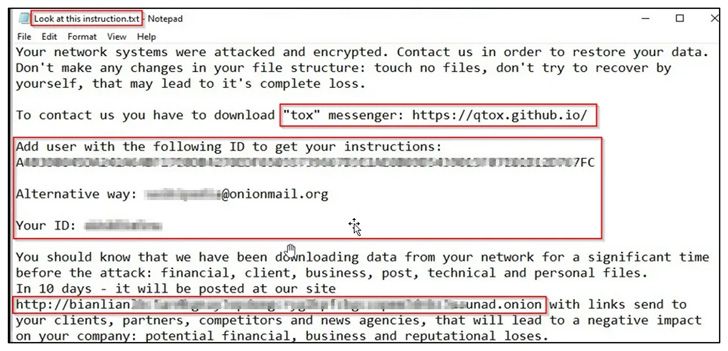
The operators of the rising cross-platform BianLian ransomware have elevated their command-and-control (C2) infrastructure this month, a growth that alludes to a rise within the group’s operational tempo.
BianLian, written within the Go programming language, was first found in mid-July 2022 and has claimed 15 sufferer organizations as of September 1, cybersecurity agency [redacted] mentioned in a report shared with The Hacker Information.
It is price noting that the double extortion ransomware household has no connection to an Android banking trojan of the identical title, which targets cellular banking and cryptocurrency apps to siphon delicate data.
Preliminary entry to sufferer networks is achieved through profitable exploitation of the ProxyShell Microsoft Change Server flaws, leveraging it to both drop an internet shell or an ngrok payload for follow-on actions.
“BianLian has additionally focused SonicWall VPN units for exploitation, one other widespread goal for ransomware teams,” [redacted] researchers Ben Armstrong, Lauren Pearce, Brad Pittack, and Danny Quist mentioned.
In contrast to one other new Golang malware known as Agenda, the BianLian actors exhibit dwell occasions of as much as six weeks from the time of preliminary entry and the precise encryption occasion, a length that is properly above the median intruder dwell time of 15 days reported in 2021.
In addition to leveraging living-off-the-land (LotL) strategies for community profiling and lateral motion, the group can be recognized to deploy a customized implant in its place means for sustaining persistent entry to the community.
The primary aim of the backdoor, per [redacted], is to retrieve arbitrary payloads from a distant server, load it into reminiscence, after which execute them.
BianLian, just like Agenda, is able to booting servers in Home windows protected mode to execute its file-encrypting malware whereas concurrently remaining undetected by safety options put in on the system.
Different steps taken to defeat safety boundaries embrace deleting shadow copies, purging backups, and operating its Golang encryptor module through Home windows Distant Administration (WinRM) and PowerShell scripts.
The earliest recognized C2 server related to BianLian is claimed to have appeared on-line in December 2021. However the infrastructure has since witnessed a “troubling explosion” to surpass 30 lively IP addresses.
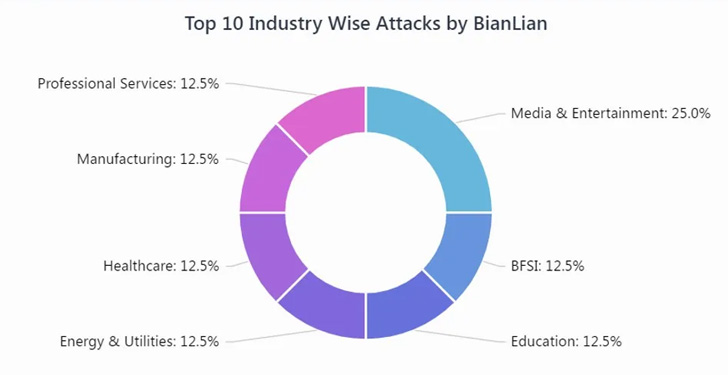
Based on Cyble, which detailed the modus operandi of the ransomware earlier this month, focused corporations span a number of trade sectors reminiscent of media, banking, vitality, manufacturing, schooling, healthcare, {and professional} companies. A majority of the businesses are primarily based in North America, the U.Okay., and Australia.
BianLian is yet one more indication of cybercriminals’ devoted efforts to proceed hopping ways in order to keep away from detection. It additionally provides to a rising variety of threats utilizing Go because the foundational language, enabling adversaries to make swift modifications in a single codebase that may then be compiled for a number of platforms.
“BianLian have proven themselves to be adept with the Dwelling of the Land (LOL) methodology to maneuver laterally, adjusting their operations primarily based on the capabilities and defenses they encountered within the community,” the researchers mentioned.

.jpg)