A brand new assault technique can be utilized to avoid internet utility firewalls (WAFs) of assorted distributors and infiltrate techniques, probably enabling attackers to realize entry to delicate enterprise and buyer info.
Internet utility firewalls are a key line of protection to assist filter, monitor, and block HTTP(S) site visitors to and from an internet utility, and safeguard towards assaults akin to cross-site forgery, cross-site-scripting (XSS), file inclusion, and SQL injection.
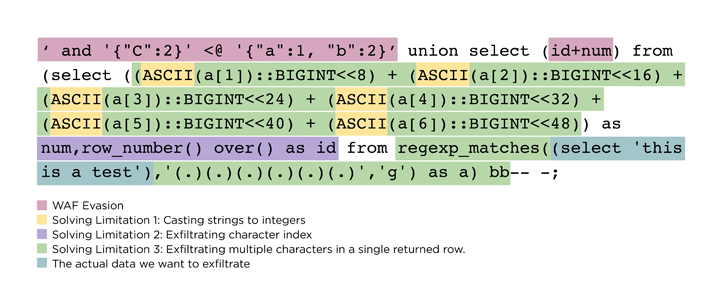
The generic bypass “entails appending JSON syntax to SQL injection payloads {that a} WAF is unable to parse,” Claroty researcher Noam Moshe stated. “Most WAFs will simply detect SQLi assaults, however prepending JSON to SQL syntax left the WAF blind to those assaults.”
The commercial and IoT cybersecurity firm stated its method efficiently labored towards WAFs from distributors like Amazon Internet Companies (AWS), Cloudflare, F5, Imperva, and Palo Alto Networks, all of whom have since launched updates to assist JSON syntax throughout SQL injection inspection.
With WAFs appearing as a safety guardrail towards malicious exterior HTTP(S) site visitors, an attacker with capabilities to get previous the barrier can get hold of preliminary entry to a goal atmosphere for additional post-exploitation.
The bypass mechanism devised by Claroty banks on the dearth of JSON assist for WAFs to craft rogue SQL injection payloads that embody JSON syntax to skirt the protections.
“Attackers utilizing this novel method may entry a backend database and use further vulnerabilities and exploits to exfiltrate info through both direct entry to the server or over the cloud,” Moshe defined. “It is a harmful bypass, particularly as extra organizations proceed emigrate extra enterprise and performance to the cloud.”