A now-patched safety flaw within the vm2 JavaScript sandbox module might be abused by a distant adversary to interrupt out of safety boundaries and carry out arbitrary operations on the underlying machine.
“A risk actor can bypass the sandbox protections to realize distant code execution rights on the host operating the sandbox,” GitHub mentioned in an advisory revealed on September 28, 2022.
The problem, tracked as CVE-2022-36067 and codenamed Sandbreak, carries a most severity ranking of 10 on the CVSS vulnerability scoring system. It has been addressed in model 3.9.11 launched on August 28, 2022.
vm2 is a standard Node library that is used to run untrusted code with allowlisted built-in modules. It is also one of the vital extensively downloaded software program, accounting for almost 3.5 million downloads per week.
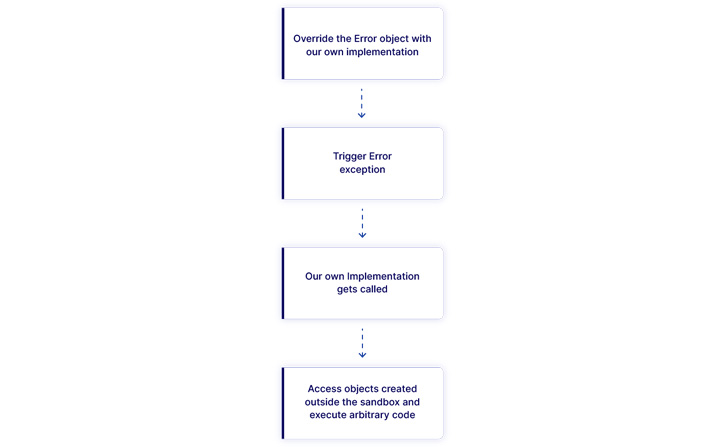
The shortcoming is rooted within the error mechanism in Node.js to flee the sandbox, in line with software safety agency Oxeye, which found the flaw.
Which means profitable exploitation of CVE-2022-36067 may allow an attacker to bypass the vm2 sandbox surroundings and run shell instructions on the system internet hosting the sandbox.
In gentle of the important nature of the vulnerability, customers are really helpful to replace to the most recent model as quickly as attainable to mitigate attainable threats.
“Sandboxes serve completely different functions in fashionable functions, equivalent to inspecting connected recordsdata in electronic mail servers, offering an extra safety layer in net browsers, or isolating actively operating functions in sure working techniques,” Oxeye mentioned.
“Given the character of the use instances for sandboxes, it is clear that the vm2 vulnerability can have dire penalties for functions that use vm2 with out patching.”