A brand new evaluation of instruments put to make use of by the Black Basta ransomware operation has recognized ties between the menace actor and the FIN7 (aka Carbanak) group.
This hyperlink “might counsel both that Black Basta and FIN7 keep a particular relationship or that a number of people belong to each teams,” cybersecurity agency SentinelOne stated in a technical write-up shared with The Hacker Information.
Black Basta, which emerged earlier this 12 months, has been attributed to a ransomware spree that has claimed over 90 organizations as of September 2022, suggesting that the adversary is each well-organized and well-resourced.
One notable facet that makes the group stand out, per SentinelOne, is the truth that there have been no indicators of its operators trying to recruit associates or promoting the malware as a RaaS on darknet boards or crimeware marketplaces.
This has raised the chance that the Black Basta builders both lower out associates from the chain and deploy the ransomware by their very own customized toolset or alternatively work with an in depth set of associates with out the necessity to market their warez.
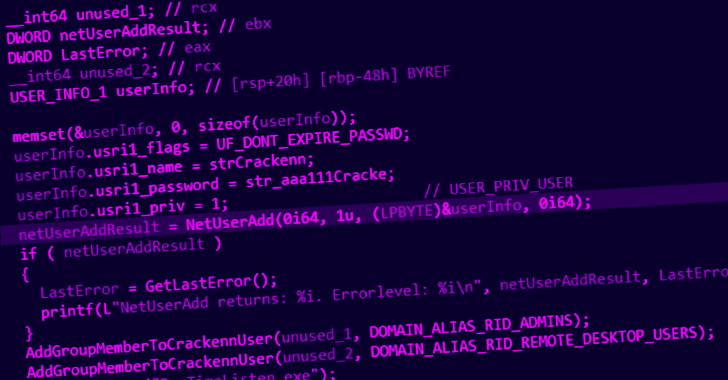
Assault chains involving Black Basta are recognized to leverage QBot (aka Qakbot), which, in flip, is delivered via phishing emails containing macro-based Microsoft Workplace paperwork, with newer infections profiting from ISO pictures and LNK droppers to get round Microsoft’s choice to dam macros in information downloaded from the online by default.
As soon as Qakbot obtains a persistent foothold within the goal setting, the Black Basta operator enters the scene to conduct reconnaissance by connecting to the sufferer by the backdoor, adopted by exploiting recognized vulnerabilities (e.g., ZeroLogon, PrintNightmare, and NoPac) to escalate privileges.
Additionally put to make use of at this stage are backdoors reminiscent of SystemBC (aka Coroxy) for information exfiltration and the obtain of further malicious modules, earlier than the conducting lateral motion and taking steps to impair defenses by disabling put in safety options.
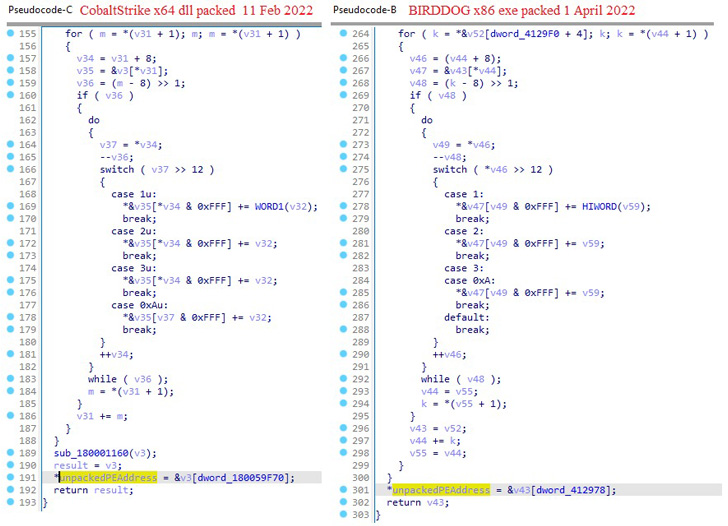
This additionally features a customized EDR evasion instrument that is been solely put to make use of in Black Basta incidents and comes embedded with a backdoor dubbed BIRDDOG, additionally known as as SocksBot and which has been utilized in a number of assaults beforehand attributed to the FIN7 group.
The FIN7 cybercrime syndicate, energetic since 2012, has a monitor file of mounting large-scale malware campaigns focusing on the point-of-sale (PoS) programs aimed on the restaurant, playing, and hospitality industries for monetary fraud.
Over the previous two years, nevertheless, the group has switched to ransomware for illicitly producing revenues, first as Darkside after which as BlackMatter and BlackCat, to not point out establishing faux entrance corporations to recruit unwitting penetration testers to stage ransomware assaults.
“At this level, it is possible that FIN7 or an affiliate started writing instruments from scratch with a purpose to disassociate their new operations from the previous,” researchers Antonio Cocomazzi and Antonio Pirozzi stated. “It’s possible that the developer(s) behind their instruments to impair sufferer defenses is, or was, a developer for FIN7.”
The findings come weeks after the Black Basta actor was noticed utilizing the Qakbot trojan to deploy Cobalt Strike and Brute Ratel C4 frameworks as a second-stage payload in latest assaults.
“The crimeware ecosystem is continually increasing, altering, and evolving,” the researchers concluded. “FIN7 (or Carbanak) is commonly credited with innovating within the legal area, taking assaults in opposition to banks and PoS programs to new heights past the schemes of their friends.”
The disclosure additionally arrives because the U.S. Monetary Crimes Enforcement Community (FinCEN) reported a surge in ransomware assaults focusing on home entities from 487 in 2020 to 1,489 in 2021, incurring a complete price of $1.2 billion, a 188% soar from $416 million the earlier 12 months.