Cybersecurity researchers have uncovered new connections between a extensively used pay-per-install (PPI) malware service referred to as PrivateLoader and one other PPI service dubbed ruzki.
“The menace actor ruzki (aka les0k, zhigalsz) advertises their PPI service on underground Russian-speaking boards and their Telegram channels below the title ruzki or zhigalsz since no less than Might 2021,” SEKOIA mentioned.
The cybersecurity agency mentioned its investigations into the dual providers led it to conclude that PrivateLoader is the proprietary loader of the ruzki PPI malware service.
PrivateLoader, because the title implies, features as a C++-based loader to obtain and deploy extra malicious payloads on contaminated Home windows hosts. It is primarily distributed by Website positioning-optimized web sites that declare to supply cracked software program.
Though it was first documented earlier this February by Intel471, it is mentioned to have been put to make use of beginning as early as Might 2021.
Among the most typical commodity malware households propagated by PrivateLoader embrace Redline Stealer, Socelars, Raccoon Stealer, Vidar, Tofsee, Amadey, DanaBot, and ransomware strains Djvu and STOP.
A Might 2022 evaluation from Development Micro uncovered the malware distributing a framework known as NetDooka. A follow-up report from BitSight late final month discovered vital infections in India and Brazil as of July 2022.
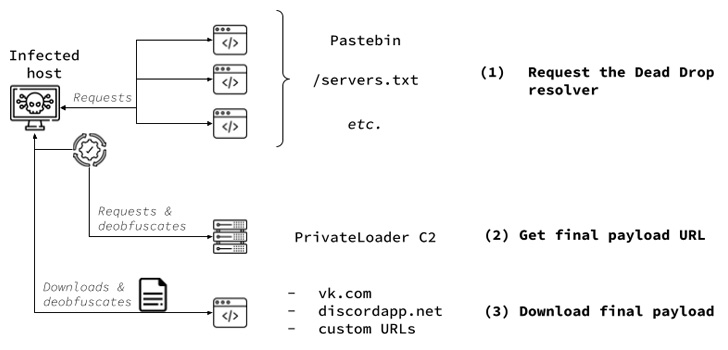
A brand new change noticed by SEKOIA is the usage of VK.com paperwork service to host the malicious payloads versus Discord, a shift probably motivated by elevated monitoring of the platform’s content material supply community.
PrivateLoader can be configured to speak with command-and-control (C2) servers to fetch and exfiltrate information. As of mid-September, there are 4 energetic C2 servers, two in Russia and one every in Czechia and Germany.
“Primarily based on the extensive choice of malware households, which means a variety of menace actors or intrusion units working this malware, the PPI service working PrivateLoader may be very engaging and well-liked to attackers on underground markets,” the researchers mentioned.
SEKOIA additional mentioned it unearthed ties between PrivateLoader and ruzki, a menace actor that sells bundles of 1,000 installations on contaminated methods situated the world over ($70), or particularly Europe ($300) or the U.S. ($1,000).
These commercials, which have been positioned within the Lolz Guru cybercrime discussion board, goal menace actors (aka potential prospects) who want to distribute their payloads by the PPI service.
The affiliation stems primarily from the under observations –
- An overlap between the PrivateLoader C2 servers and that of URLs supplied by ruzki to the subscribers in order to watch set up statistics associated to their campaigns
- References to ruzki in PrivateLoader botnet pattern names that had been used to ship the Redline Stealer, corresponding to ruzki9 and 3108_RUZKI, and
- The truth that each PrivateLoader and ruzki commenced operations in Might 2021, with the ruzki operator utilizing the time period “our loader” in Russian on its Telegram channel
“Pay-per-Set up providers at all times performed a key function within the distribution of commodity malware,” the researchers mentioned.
“As yet one more turnkey resolution decreasing the price of entry into the cybercriminal market and a service contributing to a steady professionalization of the cybercriminal ecosystem, it’s extremely probably extra PrivacyLoader-related exercise can be noticed within the quick time period.”