A brand new analysis undertaken by a bunch of lecturers from the College of California San Diego has revealed for the primary time that Bluetooth indicators might be fingerprinted to trace smartphones (and subsequently, people).
The identification, at its core, hinges on imperfections within the Bluetooth chipset {hardware} launched in the course of the manufacturing course of, leading to a “distinctive physical-layer fingerprint.”
“To carry out a physical-layer fingerprinting assault, the attacker should be geared up with a Software program Outlined Radio sniffer: a radio receiver able to recording uncooked IQ radio indicators,” the researchers mentioned in a new paper titled “Evaluating Bodily-Layer BLE Location Monitoring Assaults on Cellular Units.”
The assault is made potential because of the ubiquitous nature of Bluetooth Low Vitality (BLE) beacons which are constantly transmitted by fashionable gadgets to allow essential capabilities similar to contact tracing throughout public well being emergencies.
The {hardware} defects, alternatively, stem from the truth that each Wi-Fi and BLE elements are sometimes built-in collectively right into a specialised “combo chip,” successfully subjecting Bluetooth to the identical set of metrics that can be utilized to uniquely fingerprint Wi-Fi gadgets: service frequency offset and IQ imbalance.
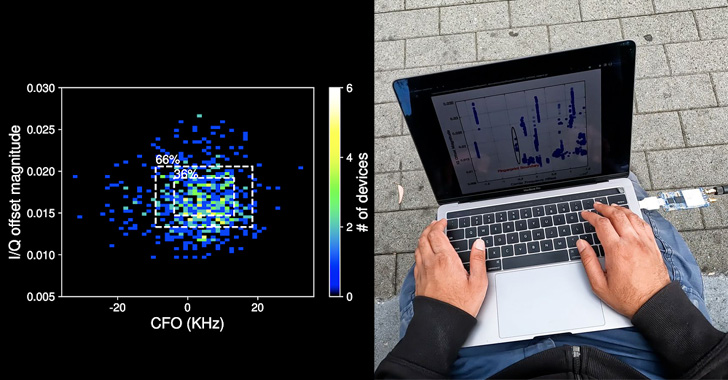
Fingerprinting and monitoring a tool then entails extracting CFO and I/Q imperfections for every packet by computing the Mahalanobis distance to find out “how shut the options of the brand new packet” are to its beforehand recorded {hardware} imperfection fingerprint.
“Additionally, since BLE gadgets have briefly secure identifiers of their packets [i.e., MAC address], we are able to establish a tool primarily based on the typical over a number of packets, growing identification accuracy,” the researchers mentioned.
That mentioned, there are a number of challenges to pulling off such an assault in an adversarial setting, chief amongst them being that the power to uniquely establish a tool depends upon the BLE chipset used in addition to the chipsets of different gadgets which are in shut bodily proximity to the goal.
Different vital elements that might have an effect on the readings embrace system temperature, variations in BLE transmit energy between iPhone and Android gadgets, and the standard of the sniffer radio utilized by the malicious actor to execute the fingerprinting assaults.
“By evaluating the practicality of this assault within the subject, notably in busy settings similar to espresso retailers, we discovered that sure gadgets have distinctive fingerprints, and subsequently are notably weak to monitoring assaults, others have frequent fingerprints, they’ll typically be misidentified,” the researchers concluded.
“BLE does current a location monitoring risk for cellular gadgets. Nonetheless an attacker’s skill to trace a selected goal is basically a matter of luck.”