Microsoft on Tuesday mentioned it addressed an authentication bypass vulnerability in Jupyter Notebooks for Azure Cosmos DB that enabled full learn and write entry.
The tech big mentioned the issue was launched on August 12, 2022, and rectified worldwide on October 6, 2022, two days after accountable disclosure from Orca Safety, which dubbed the flaw CosMiss.
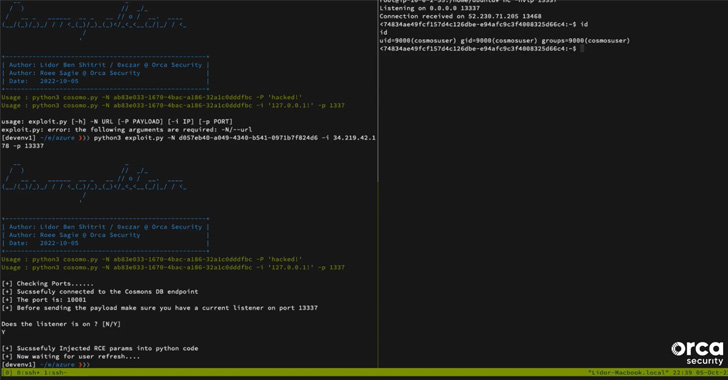
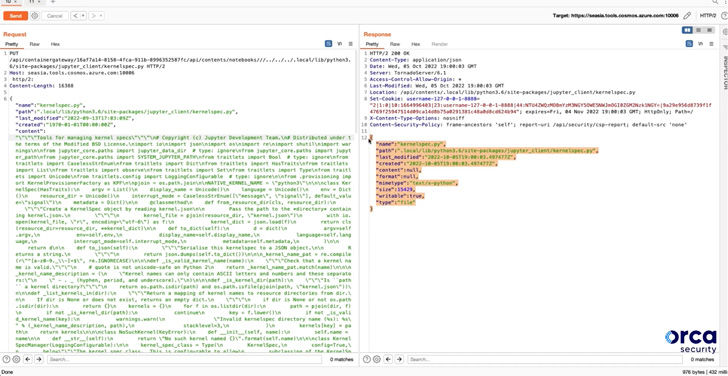
“Briefly, if an attacker had information of a Pocket book’s ‘forwardingId,’ which is the UUID of the Pocket book Workspace, they might have had full permissions on the Pocket book with out having to authenticate, together with learn and write entry, and the power to change the file system of the container operating the pocket book,” researchers Lidor Ben Shitrit and Roee Sagi mentioned.
This container modification may in the end pave the way in which for acquiring distant code execution within the Pocket book container by overwriting a Python file related to the Cosmos DB Explorer to spawn a reverse shell.
Profitable exploitation of the flaw, nonetheless, requires that the adversary is in possession of the distinctive 128-bit forwardingId and that it is put to make use of inside a one-hour window, after which the non permanent Pocket book is robotically deleted.
“The vulnerability, even with information of the forwardingId, didn’t give the power to execute notebooks, robotically save notebooks within the sufferer’s (non-obligatory) linked GitHub repository, or entry to knowledge within the Azure Cosmos DB account,” Redmond mentioned.
Microsoft famous in its personal advisory that it recognized no proof of malicious exercise, including no motion is required from prospects. It additionally described the difficulty as “tough to take advantage of” owing to the randomness of the 128 bit forwadingID and its restricted lifespan.
“Prospects not utilizing Jupyter Notebooks (99.8% of Azure Cosmos DB prospects do NOT use Jupyter notebooks) weren’t prone to this vulnerability,” it additional mentioned.