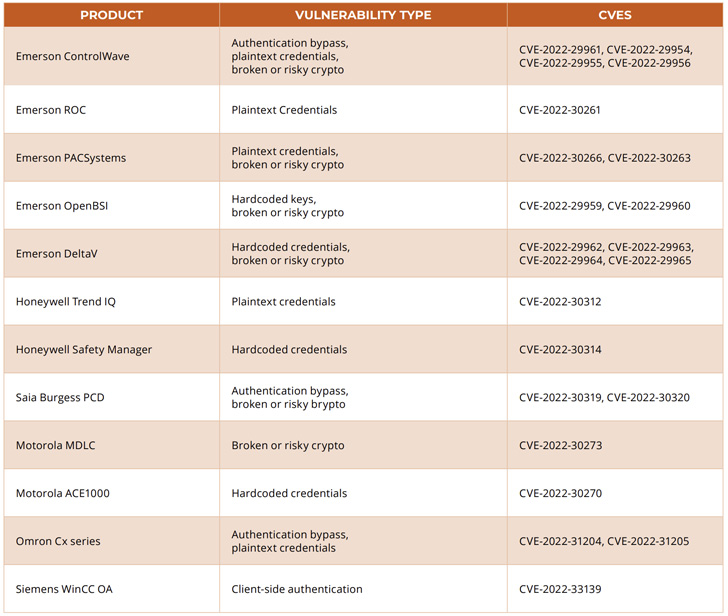
Practically 5 dozen safety vulnerabilities have been disclosed in units from 10 operational expertise (OT) distributors as a result of what researchers name are “insecure-by-design practices.”
Collectively dubbed OT:ICEFALL by Forescout, the 56 points span as many as 26 system fashions from Bently Nevada, Emerson, Honeywell, JTEKT, Motorola, Omron, Phoenix Contact, Siemens, and Yokogawa.
“Exploiting these vulnerabilities, attackers with community entry to a goal system might remotely execute code, change the logic, recordsdata or firmware of OT units, bypass authentication, compromise credentials, trigger denials of service or have quite a lot of operational impacts,” the corporate mentioned in a technical report.
These vulnerabilities might have disastrous penalties contemplating the impacted merchandise are broadly employed in essential infrastructure industries comparable to oil and fuel, chemical, nuclear, energy era and distribution, manufacturing, water remedy and distribution, mining, and constructing automation.
Of the 56 vulnerabilities found, 38% enable for compromise of credentials, 21% enable for firmware manipulation, 14% enable distant code execution, and eight% of flaws allow tampering with configuration info.
Apart from doubtlessly allowing an attacker to produce arbitrary code and make unauthorized modifications to the firmware, the weaknesses may be leveraged to take a tool utterly offline and bypass current authentication features to invoke any performance on the targets.
Extra importantly, damaged authentication schemes — together with bypass, use of dangerous cryptographic protocols, and hardcoded and plaintext credentials — accounted for 22 of the 56 flaws, indicating “subpar safety controls” throughout implementation.
In a hypothetical real-world situation, these shortcomings may very well be weaponized in opposition to pure fuel pipelines, wind generators, or discrete manufacturing meeting strains to disrupt gasoline transport, override security settings, halt the power to regulate compressor stations, and alter the functioning of programmable logic controllers (PLCs).
However the threats should not simply theoretical. A distant code execution flaw affecting Omron NJ/NX controllers (CVE-2022-31206) was, actually, exploited by a state-aligned actor dubbed CHERNOVITE to develop a chunk of a complicated malware named PIPEDREAM (aka INCONTROLLER).
Complicating danger administration is the rising interconnectedness between IT and OT networks, coupled with the opaque and proprietary nature of many OT methods, to not point out the absence of CVEs, rendering the lingering points invisible in addition to retaining such insecure-by-design options for a very long time.
To mitigate OT:ICEFALL, it is beneficial to find and stock weak units, implement segmentation of OT property, monitor community site visitors for anomalous exercise, and procure secure-by-design merchandise to beef up the availability chain.
“The event of current malware focusing on essential infrastructure, comparable to Industroyer2, Triton, and INCONTROLLER, has proven that menace actors are conscious of the insecure by design nature of operational expertise and are prepared to take advantage of it to wreak havoc,” the researchers mentioned.
“Regardless of the necessary function that standards-driven hardening efforts play in OT safety, merchandise with insecure-by-design options and trivially damaged safety controls continued to be licensed.”