An ongoing evaluation into an up-and-coming cryptocurrency mining botnet generally known as KmsdBot has led to it being by chance taken down.
KmsdBot, as christened by the Akamai Safety Intelligence Response Staff (SIRT), got here to gentle mid-November 2022 for its skill to brute-force methods with weak SSH credentials.
The botnet strikes each Home windows and Linux gadgets spanning a variety of microarchitectures with the first purpose of deploying mining software program and corralling the compromised hosts right into a DDoS bot.
A number of the main targets included gaming corporations, expertise corporations, and luxurious automotive producers.
Akamai researcher Larry W. Cashdollar, in a brand new replace, defined how instructions despatched to the bot to grasp its performance in a managed atmosphere inadvertently neutralized the malware.
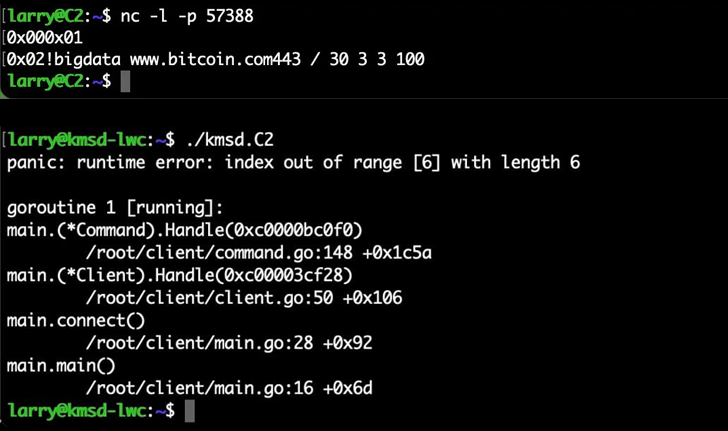
“Apparently, after one single improperly formatted command, the bot stopped sending instructions,” Cashdollar mentioned. “It is not each day you come throughout a botnet that the risk actors themselves crash their very own handiwork.”
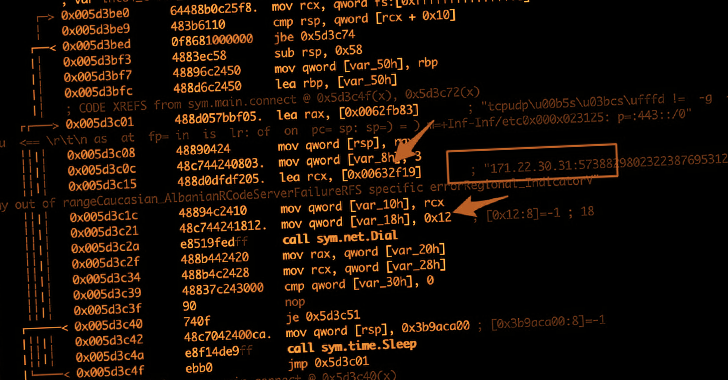
This, in flip, was made attainable because of the lack of an error-checking mechanism constructed into the supply code to validate the acquired instructions.
Particularly, an instruction issued and not using a house between the goal web site and the port precipitated the complete Go binary working on the contaminated machine to crash and cease interacting with its command-and-control server, successfully killing the botnet.
The truth that KmsdBot does not have a persistence mechanism additionally signifies that the malware operator should re-infect the machines once more and re-build the infrastructure from scratch.
“This botnet has been going after some very massive luxurious manufacturers and gaming corporations, and but, with one failed command it can’t proceed,” Cashdollar concluded. “This can be a robust instance of the fickle nature of expertise and the way even the exploiter might be exploited by it.”