We wrote final week about analysis displaying that Meta takes benefit of the in-app browser function on cellular units to inject JavaScript into net pages seen within the Fb, Instagram, and Messenger cellular apps. Now that very same researcher has discovered that the TikTok in-app browser injects JavaScript which capabilities just like a keylogger to report all keyboard inputs and faucets on web page components.
Many cellular apps let customers click on on hyperlinks and go to the linked webpages throughout the app, quite than opening the system’s default browser app. Apple provides a restricted Safari viewport that builders can embrace of their iOS apps for this objective. Nevertheless, builders can even create their very own in-app browsers, and it seems that some builders construct their very own in-app browsers to inject JavaScript into webpages.
Felix Krause first found this habits in Meta cellular apps, however he didn’t cease his looking out there. After growing a rudimentary software to detect JavaScript injection for his analysis on Meta apps, the researcher determined to develop this software into one which can be utilized by the general public. He then went to work testing extra in-app browsers with this software. What this additional analysis reveals is that TikTok’s in-app browser injects much more invasive code than the in-app browsers in Meta apps.
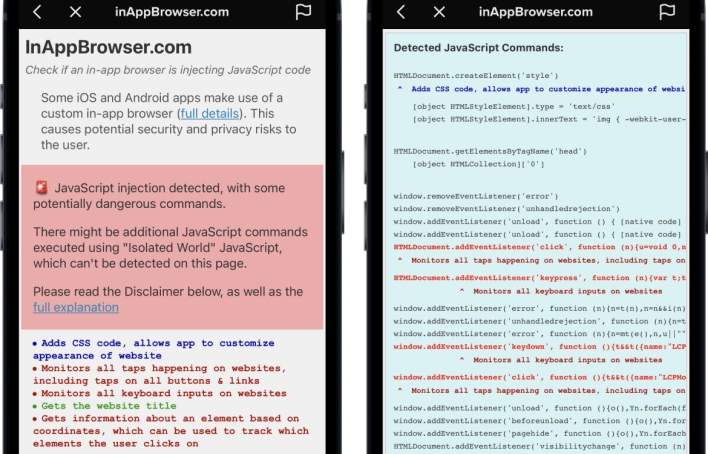
Krause’s JavaScript injection software revealed that TikTok’s in-app browser injects code that listens for each key enter entered into webpages seen throughout the app. Because of this TikTok may probably report all textual content, together with passwords, bank card particulars, and some other delicate info entered into web sites accessed by the use of its in-app browser. The TikTok cellular app additionally injects code that may detect each faucet on webpage components, resembling buttons, hyperlinks, and pictures, and skim the title of every factor as customers work together with it. Along with injecting this JavaScript, in contrast to many different in-app browsers, TikTok’s in-app browser doesn’t embrace an choice permitting customers to open webpages of their units’ default browsers. Thus, if customers need to keep away from TikTok’s in-app browser, they must manually copy hyperlinks proven within the app and paste them into the browser app of their alternative.
In an announcement reported by Forbes, Maureen Shanahan, a spokesperson for TikTok, acknowledged that its in-app browser injects code, however stated that it has a reliable use. “Like different platforms, we use an in-app browser to supply an optimum consumer expertise, however the Javascript code in query is used just for debugging, troubleshooting and efficiency monitoring of that have — like checking how shortly a web page masses or whether or not it crashes.”
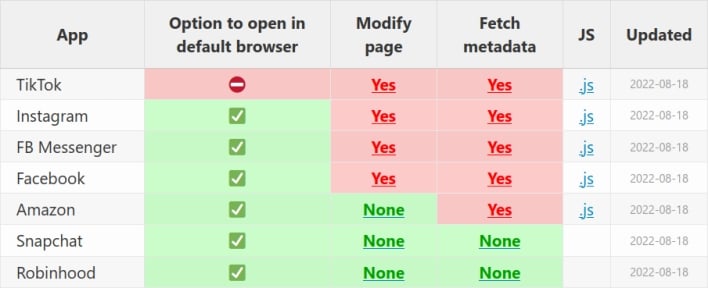
We will’t assist however be skeptical of this assertion when TikTok has a historical past of going to nice lengths to entry and accumulate consumer info. The TikTok app has beforehand monitored iOS customers’ keyboards, even after the corporate promised to take away this habits, exploited a safety vulnerability to uniquely establish Android units, and said that it might accumulate faceprints and voiceprints. This extreme assortment of consumer information is especially regarding on condition that leaked audio recordings not too long ago revealed that US TikTok workers don’t have a very good deal with on the place consumer information goes. Some US TikTok information scientists nonetheless obtain direct orders from ByteDance’s fundamental workplace in Beijing, China, prompting an FCC Commissioner to publish a letter asking Apple and Google to ban TikTok from their app shops.

