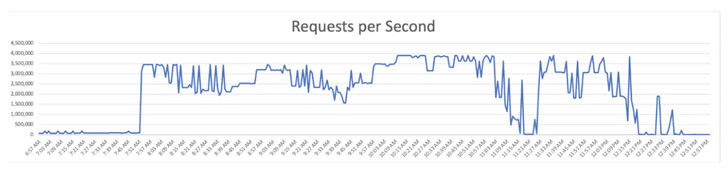
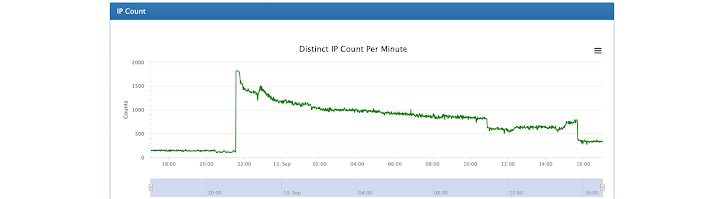
Cybersecurity firm Imperva has disclosed that it mitigated a distributed denial-of-service (DDoS) assault with a complete of over 25.3 billion requests on June 27, 2022.
The “sturdy assault,” which focused an unnamed Chinese language telecommunications firm, is claimed to have lasted for 4 hours and peaked at 3.9 million requests per second (RPS).
“Attackers used HTTP/2 multiplexing, or combining a number of packets into one, to ship a number of requests without delay over particular person connections,” Imperva mentioned in a report revealed on September 19.
The assault was launched from a botnet that comprised practically 170,000 completely different IP addresses spanning routers, safety cameras, and compromised servers situated in additional than 180 nations, primarily the U.S., Indonesia, and Brazil.
The disclosure additionally comes as net infrastructure supplier Akamai mentioned it fielded a brand new DDoS assault aimed toward a buyer based mostly in Jap Europe on September 12, with assault site visitors spiking at 704.8 million packets per second (pps).
The identical sufferer was beforehand focused on July 21, 2022, similarly during which the assault quantity ramped as much as 853.7 gigabits per second (Gbps) and 659.6 million pps over a interval of 14 hours.
Akamai’s Craig Sparling mentioned the corporate has been “bombarded relentlessly with subtle distributed denial-of-service (DDoS) assaults,” indicating that the offensives may very well be politically motivated within the face of Russia’s ongoing battle towards Ukraine.
Each the disruptive makes an attempt have been UDP flood assaults the place the attacker targets and overwhelms arbitrary ports on the goal host with Consumer Datagram Protocol (UDP) packets.
UDP, being each connectionless and session-less, makes it an excellent networking protocol for dealing with VoIP site visitors. However these similar traits also can render it extra vulnerable to exploitation.
“With out an preliminary handshake to make sure a official connection, UDP channels can be utilized to ship a big quantity of site visitors to any host,” NETSCOUT says.
“There aren’t any inside protections that may restrict the speed of a UDP flood. In consequence, UDP flood DoS assaults are exceptionally harmful as a result of they are often executed with a restricted quantity of assets.”