ACM.42 Constant naming results in simplified code
This can be a continuation of my sequence on Automating Cybersecurity Metrics.
In my final two posts I wrote about naming conventions for cloud sources and why a well-thought-out naming conference could be useful.
Let’s take a look at some refactoring we are able to do to create a standard naming conference for our IAM admins.
Camel Case and Constant Names in CloudFormation
I wrote about utilizing camel case in CloudFormation within the final put up. I made the next adjustments to this CloudFormation template:
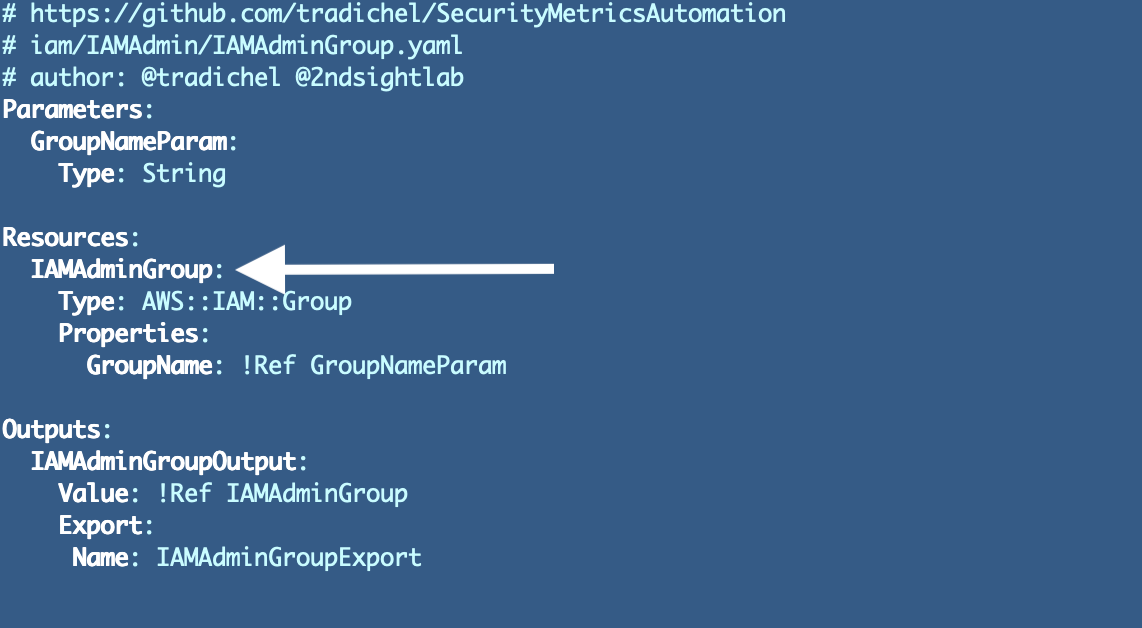
Format the useful resource identify in camel case and added kind on the finish:

Why: We will’t use symbols right here as defined within the final put up. Camel case is a bit simpler to learn that each one higher or all decrease case. Including the kind to the tip will make this useful resource simpler to establish in a number of locations the place you could be looking for the code, sources, or CloudFormation stacks that created these sources.
Initially I renamed the recordsdata to match the useful resource identify. Be aware that this will get additional revisions within the subsequent put up.

Why: This makes it simpler to search out the code associated to a stack or a useful resource in my supply code repository.
I renamed parameters, outputs, and exports to camel case format and added the kind on the finish:
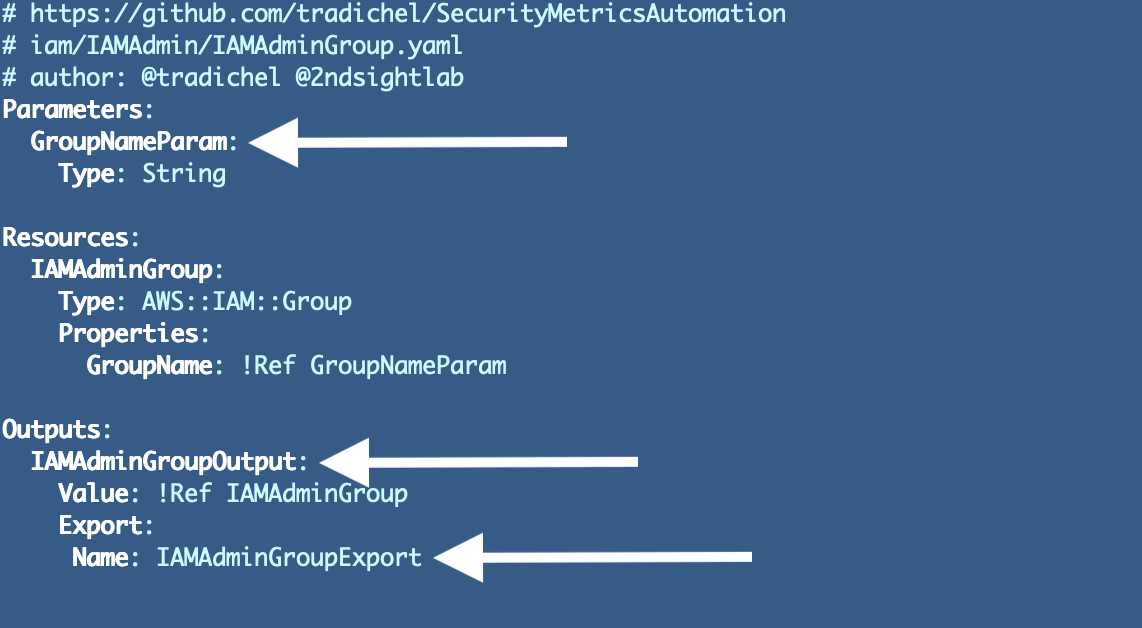
Why: Readability and consistency for one factor. Moreover, I’ve run into points prior to now the place confusion between these things once they all had the identical identify brought about troubleshooting to take lengthy. Figuring out the kind clearly will assist stop errors.
I added the GitHub repository location.

Why: This makes it simpler to determine the place the code got here from. Inside a corporation it ought to inform you who wrote the template and the repository from which the code acquired deployed if you want to test the change historical past or do another kind of investigation. You can even test for drift to make sure that what’s deployed matches the present supply code.
Subsequent we have to alter the deploy template that deploys our templates.
The very first thing I did was add the prefix that we’re going to make use of with our templates which, on this case, is IAM. I made a decision to make use of higher and decrease case for my CloudFormation template stack names as a result of actually the one factor that we are able to’t use higher case for that I do know of on AWS are S3 buckets. They must be our anomaly. Half decrease and half camel case simply seems to be bizarre to me. I like to write down fairly code.

The useful resource identify for every stack matched the template identify and the useful resource within the CloudFormation template initially. Because it seems we are able to scale back the variety of templates we create so there’s not at all times a one-to-one mapping. I’ll change that for sure sources within the subsequent put up, but when we’re utilizing a one-off template the template and useful resource names ought to usually match.
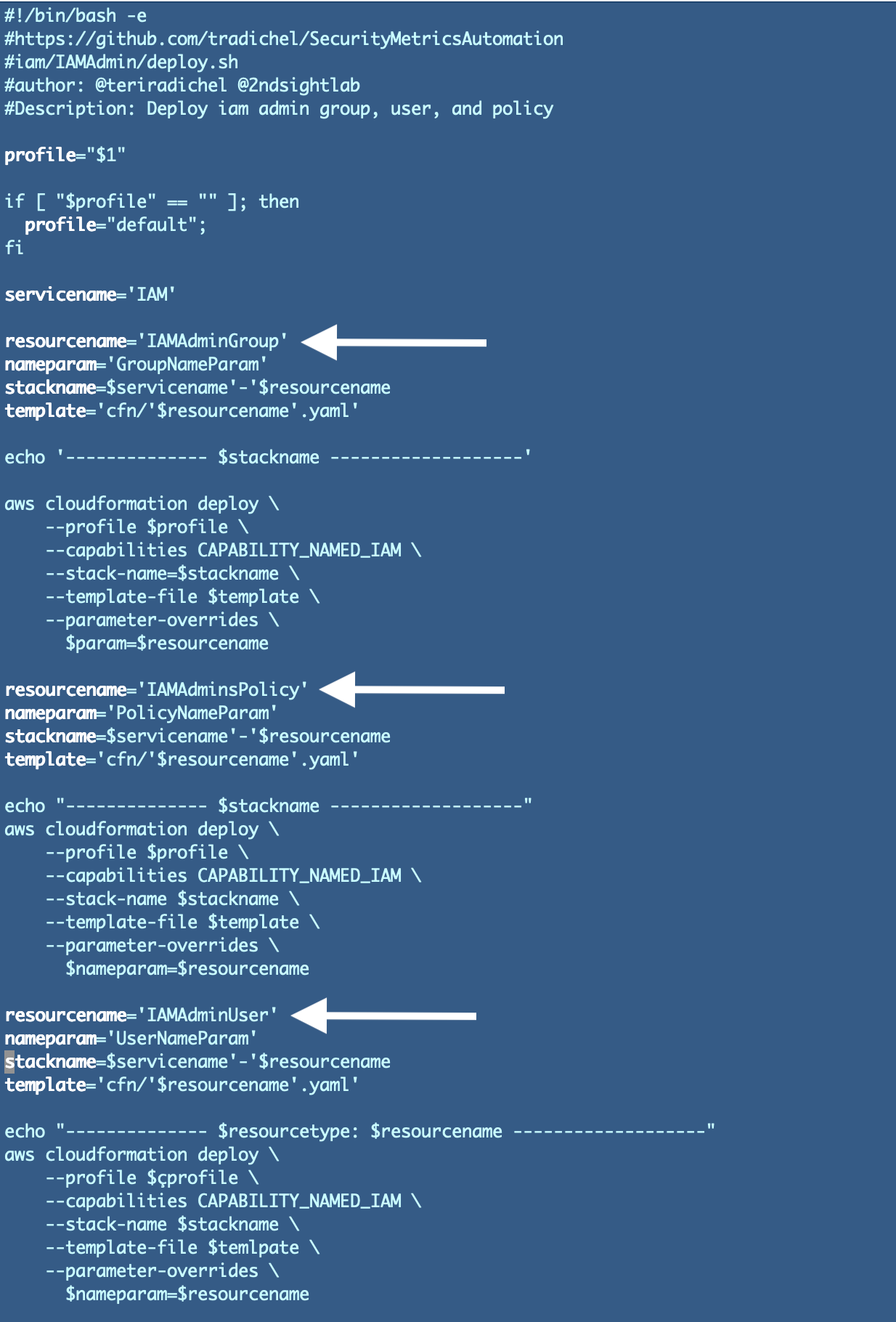
Initially I simply made the useful resource kind a part of the identify however I did find yourself altering that to match my prior naming conventions later. Maintain that thought as a result of I need to clarify one thing else on this weblog put up.
Subsequent I want to vary my deployment template.
Be aware that since my file names now match my useful resource names, I can calculate the template file identify:

Why: Utilizing variables will assist keep consistency and forestall typos in names and recordsdata.
I also can calculate a constant stack identify with the prefix and the useful resource identify:

Why: Utilizing variables will assist keep consistency and forestall typos in stack names. I also can doubtlessly use the constant naming conference in IAM Insurance policies.
Properly, that’s neat however do you discover something in regards to the deploy script that might probably be cleaned up and simplified? That is the primary level I need to clarify on this put up.
Discover that we’re repeating very comparable code again and again now. We may create a regular perform to deal with the deployment of our stack and thereby scale back code and forestall bugs. Confer with the DRY precept I wrote about in my sequence on safe coding:
We may create a perform that takes widespread parameters and formulates our stack identify for us.
I went by way of just a few iterations earlier than I got here up with the next perform. I made the parameters argument a string for many flexibility and least complication. We’ll rely on the code that passes the arguments to this perform to validate them correctly, and the AWS CLI code.
For an IAM stack we have to embrace the CAPABILITY_NAMED_IAM. We received’t want that for different varieties of stacks so I created a separate perform for IAM deployments. Presuming those who use the perform cross within the right parameters, IAM stacks will begin with “IAM” adopted by the useful resource kind after which the identify of the useful resource.

The result’s persistently named stacks:

I’ll present you the way I used the brand new widespread perform within the subsequent put up and additional organized the code. We wish the code to be as reusable as potential whereas nonetheless making it straightforward for somebody to search out the code that deployed a stack.
Teri Radichel
For those who favored this story please clap and observe:
Medium: Teri Radichel or Electronic mail Checklist: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests providers through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this sequence:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Sources by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, displays, and podcasts