Recon is among the most vital phases that appear straightforward however takes lots of effort and ability to do proper. One must find out about the precise instruments, appropriate queries/syntax, run these queries, correlate the data, and sanitize the output. All of this is perhaps straightforward for a seasoned infosec/recon skilled to do, however for relaxation, it’s nonetheless close to to magic. How cool will probably be to ask a easy query like “Discover me an open Memcached server in Singapore with UDP assist?” or “What number of IP cameras in Singapore are utilizing default credentials?” in a chat and get the reply?
The mixing of GPT-3, deep learning-based language fashions to supply human-like textual content, with well-known recon instruments like Shodan, is the inspiration of ReconPal. ReconPal additionally helps utilizing voice instructions to execute widespread exploits and carry out reconnaissance.
Constructed With
- OpenAI GPT-3
- Shodan API
- Speech-to-Textual content
- Telegram Bot
- Docker Containers
- Python 3
To get ReconPal up and working, comply with these easy steps.
Conditions
Set up
-
Clone the repo
git clone https://github.com/pentesteracademy/reconpal.git -
Enter your OPENAI, SHODAN API keys, and TELEGRAM bot token in
docker-compose.ymlOPENAI_API_KEY=<Your key>
SHODAN_API_KEY=<Your key>
TELEGRAM_BOT_TOKEN=<Your token> -
Begin reconpal
Open the telegram app and choose the created bot to make use of ReconPal.
- Click on on begin or simply kind within the enter field.
- Register the mannequin.
- Check the instrument with some instructions.
Jeswin Mathai, Senior Safety Researcher, INE [email protected]
Nishant Sharma, Safety Analysis Supervisor, INE [email protected]
Shantanu Kale, Cloud Developer, INE [email protected]
Sherin Stephen, Cloud Developer, INE [email protected]
Sarthak Saini (Ex-Pentester Academy)
For extra particulars, check with the “ReconPal.pdf” PDF file. This file accommodates the slide deck used for shows.
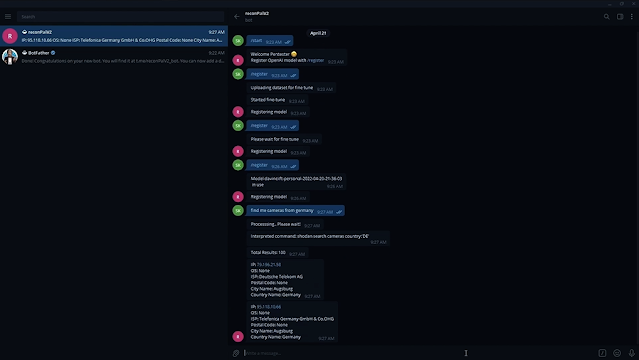
Beginning reconpal and registering mannequin
Finder module in motion
Scanner module in motion
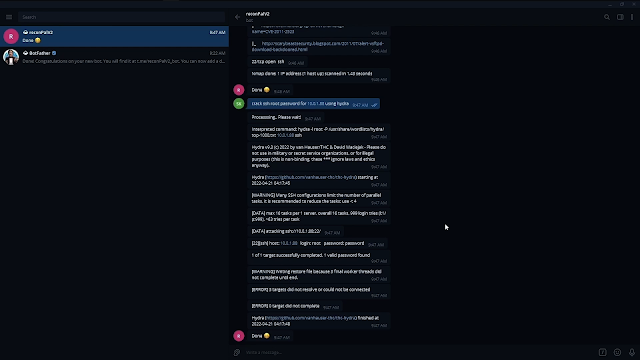
Attacker module in motion
Voice Assist
This program is free software program: you possibly can redistribute it and/or modify it underneath the phrases of the GNU Normal Public License v2 as printed by the Free Software program Basis.
This program is distributed within the hope that will probably be helpful, however WITHOUT ANY WARRANTY; with out even the implied guarantee of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU Normal Public License for extra particulars.
You must have obtained a duplicate of the GNU Normal Public License together with this program. If not, see http://www.gnu.org/licenses/.