The Raspberry Robin worm is turning into an access-as-a-service malware for deploying different payloads, together with IcedID, Bumblebee, TrueBot (aka Silence), and Clop ransomware.
It’s “a part of a posh and interconnected malware ecosystem, with hyperlinks to different malware households and alternate an infection strategies past its authentic USB drive unfold,” the Microsoft Safety Menace Intelligence Middle (MSTIC) mentioned in an in depth write-up.
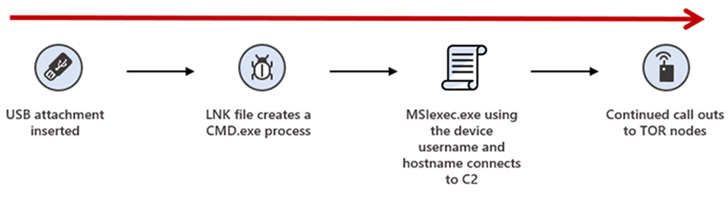
Raspberry Robin, additionally known as QNAP Worm owing to the usage of compromised QNAP storage servers for command-and-control, is the identify given to a malware by cybersecurity firm Crimson Canary that spreads to Home windows techniques by contaminated USB drives.
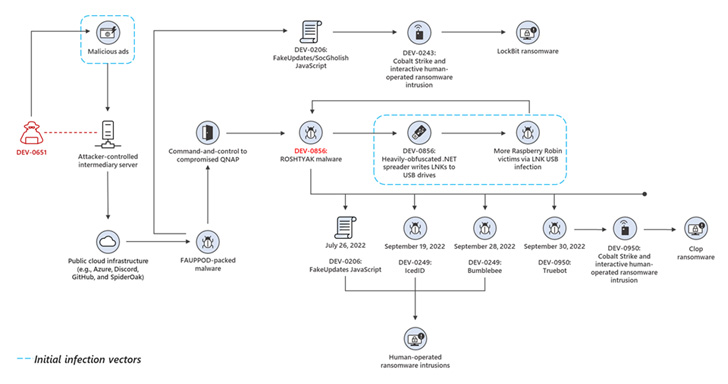
MSTIC is protecting tabs on the exercise group behind the USB-based Raspberry Robin infections as DEV-0856, including it is conscious of not less than 4 confirmed entry factors that each one have the possible finish aim of deploying ransomware.
The tech large’s cybersecurity workforce mentioned that Raspberry Robin has advanced from a broadly distributed worm with no noticed post-infection actions to one of many largest malware distribution platforms presently energetic.
In keeping with telemetry knowledge collected from Microsoft Defender for Endpoint, roughly 3,000 gadgets spanning almost 1,000 organizations have encountered not less than one Raspberry Robin payload-related alert within the final 30 days.
The newest improvement provides to rising proof of post-exploitation actions linked to Raspberry Robin, which, in July 2022, was found performing as a conduit to ship the FakeUpdates (aka SocGholish) malware.
This FakeUpdates exercise has additionally been adopted by pre-ransomware habits attributed to a risk cluster tracked by Microsoft as DEV-0243 (aka Evil Corp), the notorious Russian cybercrime syndicate behind the Dridex trojan and a command-and-control (C2) framework known as TeslaGun.
Microsoft, in October 2022, mentioned it detected Raspberry Robin being utilized in post-compromise exercise attributed to a special risk actor it has codenamed DEV-0950 and which overlaps with teams monitored publicly as FIN11 and TA505.
Whereas the names FIN11 and TA505 have usually been used interchangeably, Google-owned Mandiant (previously FireEye) describes FIN11 as a subset of exercise below the TA505 group.
It is also price stating the conflation of Evil Corp and TA505, though Proofpoint assesses “TA505 to be completely different than Evil Corp,” suggesting that these clusters share partial tactical commonalities with each other.
“From a Raspberry Robin an infection, the DEV-0950 exercise led to Cobalt Strike hands-on-keyboard compromises, typically with a TrueBot an infection noticed in between the Raspberry Robin and Cobalt Strike stage,” the researcher mentioned. “The exercise culminated in deployments of the Clop ransomware.”
Microsoft additionally theorized that the actors behind these Raspberry Robin-related malware campaigns are paying the worm’s operators for payload supply, enabling them to maneuver away from phishing as a vector to amass new victims.
What’s extra, a cybercriminal actor dubbed DEV-0651 has been linked to the distribution of one other artifact known as Fauppod by the abuse of professional cloud providers, which reveals code similarities to Raspberry Robin and likewise drops the FakeUpdates malware.
The Home windows maker additional famous wih medium confidence that Fauppod represents the earliest recognized hyperlink within the Raspberry Robin an infection chain for propagating the latter by way of LNK recordsdata to USB drives.
So as to add to the assault puzzle, IBM Safety X-Power, early final month, recognized practical similarities between a loader element used within the Raspberry Robin an infection chain and the Dridex malware. Microsoft is attributing this code-level connection to Fauppod adopting Dridex’s strategies to keep away from execution in particular environments.
“Raspberry Robin’s an infection chain is a complicated and difficult map of a number of an infection factors that may result in many various outcomes, even in situations the place two hosts are contaminated concurrently,” Microsoft mentioned.