Risk actors affiliated with a ransomware pressure referred to as Play are leveraging a never-before-seen exploit chain that bypasses blocking guidelines for ProxyNotShell flaws in Microsoft Trade Server to attain distant code execution (RCE) by way of Outlook Net Entry (OWA).
“The brand new exploit technique bypasses URL rewrite mitigations for the Autodiscover endpoint,” CrowdStrike researchers Brian Pitchford, Erik Iker, and Nicolas Zilio mentioned in a technical write-up printed Tuesday.
Play ransomware, which first surfaced in June 2022, has been revealed to undertake many techniques employed by different ransomware households comparable to Hive and Nokoyawa, the latter of which upgraded to Rust in September 2022.
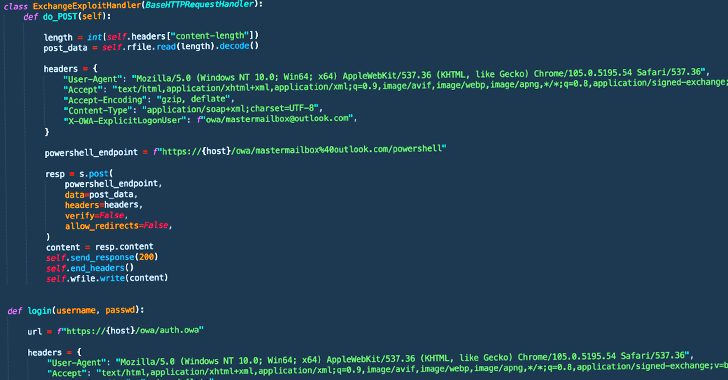
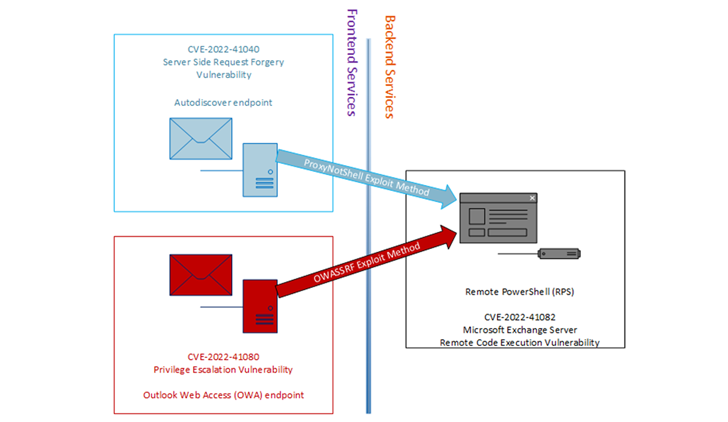
The cybersecurity firm’s investigations into a number of Play ransomware intrusions discovered that preliminary entry to the goal environments was not achieved by immediately exploiting CVE-2022-41040, however reasonably by way of the OWA endpoint.
Dubbed OWASSRF, the approach seemingly takes benefit of one other essential flaw tracked as CVE-2022-41080 (CVSS rating: 8.8) to attain privilege escalation, adopted by abusing CVE-2022-41082 for distant code execution.
It is value noting that each CVE-2022-41040 and CVE-2022-41080 stem from a case of server-side request forgery (SSRF), which allows an attacker to entry unauthorized inner assets, on this case the PowerShell remoting service.
CrowdStrike mentioned the profitable preliminary entry enabled the adversary to drop legit Plink and AnyDesk executables to keep up persistent entry in addition to take steps to purge Home windows Occasion Logs on contaminated servers to hide the malicious exercise.
All three vulnerabilities had been addressed by Microsoft as a part of its Patch Tuesday updates for November 2022. It is, nevertheless, unclear if CVE-2022-41080 was actively exploited as a zero-day alongside CVE-2022-41040 and CVE-2022-41082.
The Home windows maker, for its half, has tagged CVE-2022-41080 with an “Exploitation Extra Doubtless” evaluation, implying it is doable for an attacker to create exploit code that may very well be utilized to reliably weaponize the flaw.
CrowdStrike additional famous {that a} proof-of-concept (PoC) Python script found and leaked by Huntress Labs researcher Dray Agha final week might have been put to make use of by the Play ransomware actors for preliminary entry.
That is evidenced by the truth that the execution of the Python script made it doable to “replicate the logs generated in current Play ransomware assaults.”
“Organizations ought to apply the November 8, 2022 patches for Trade to stop exploitation because the URL rewrite mitigations for ProxyNotShell usually are not efficient towards this exploit technique,” the researchers mentioned.